1. Introduction to CyberSecurity
Information Security: it is the protection of the information and how it is modify. Information System Security: protecting the systems that access the information.
1.1 CIA Triad
These are the core values we should always have:
- Confidentiality: ensure that info has not been disclose to unauthorized people; these include keys and passwords that allows to protect the information.
- Integrity: ensuring that the information has not been modified without authorization; if we could go to a bank website and modify our balance that would be an availability failure; we can use hashes for this purpose.
- Availability: being able to access the information when needed.
1.2 AAA of Security
There are 3 main values:
- Authentication: when a person's identity is establish with proof; we have 5
methods:
- Something you know.
- Something you are.
- Something you have.
- Something you do.
- Somewhere you are.
- Authorization: when an user is given access to access a certain part of a place.
- Accounting: these trackers data and computer resources; for this we use logs, this allows us to know who and what they did. Non-repudiation is when the user can not say "I did not do it", because I have the proof you did so.
1.3 Security Threat
The 4 main categories are:
- Malware: malicious software such as adware, randomsware, virus, etc.
- Unauthorize access: gain access to computer resources or data without the consent by breaching the security.
- System Failure: when a computer crashes.
- Social Engineering: manipulating users to reveal confidential information, it usually happens by phishing emails.
1.4 Mitigating Threats
There are controls that can help us: Physical controls: alarms, security cameras, batches id. Technical controls: smart cards, intrusion detection, etc. Administrative controls: policies, security awarennes, contingency planning; these can be divided by those that are mandatory by law because of the nature of the company, and on the other hand those that are implemented by the company; these can also be call managerial controls. It is important to use all of these.
1.5 Hackers
Types of hackers:
- White Hat: somebody non malicious, who tries to access the systems with authorization in order to test the security.
- Black Hat: someone malicious who breaks in computers os systems without permission.
- Gray Hat: it is a hacker who breaks without authorization but they do not want to steal the data nor do something malicious; they are in the middle.
- Blue Hat: tries to break a systems but have not been hired, for example bug bounty hunters.
- Elite: those who find and exploits vulnerabilities before anyone does, they program their own tools, exploits and attacks. They are very very good and can be malicious or no malicious, it is estimate that only 1 of 10000 hackers are elite hackers. These are the best of the best.
1.6 Threat Actors
- Script Kiddies: baby hackers that only uses automatic tools, they do not have skills and do not even know what the tools do. This is how many of us start.
- Hacktivists: hackers who are drive by social causes, for example anonymous. They are those who only uses any tool available trying to find anything they can, they do not know how the tool works; these the babies of hackers.
- Organize crime: organization who are very well funded, they usually do it for the money, for example the ransomware groups.
- Advance Persist Threats: highly trained hackers, usually from governments, for example China or Russia. They are very good and when gain access they usually do little to no noise and are difficult to detect.
1.7 Threat Intelligence
- Time: the information it is important with the relavancy of time, as things change.
- Relevance: that the intelligence matches the case intented and what affects me.
- Accuracy: makes that the informaiton produces effective results, it is important that the information is not false positives.
- Confidence leves: ensures qualified statements about the reliability of an information, are the things relavant and reliable.
1.8 Threat Hunting
It is a technique to detect the present of threats that have not been identify, the idea is to be proactive instead of being reactive (most of what the SOC does). We establish a hypothesis and start our path, asking who may want to attacks us, and then using the intelligence we can have an idea who may be doing the attacks. We analyze logs and others from monitoring tools; when we are threat hunting, we need to assume that the existing rules have failed and therefore things that have bypass the rules, assuming that the adversary is smart and avoiding detection. Threat hunting consumes a lot of resources and time in order to detect something. With the threat hunting results we can then:
- Improve detection capabilities.
- Integrate intelligence.
- Reduce attack surface.
- Block attack vectors.
- Identify critical assets so we know what attackers are after to.
1.9 Attack Framework
The kill chain is:
- Reconnaissance: the attackers need to find out what methods they need to attack us; after this we need to have an idea of this network is build.
- Weaponization: the attacker creates payloads to exploit vulnerabilities in the system.
- Delivery: the attacker uses a method to get the payload to the system, using whatever method they can such as email.
- Exploitation: is when the malicious code is executed in the system.
- Installation: it is a mechanism that enables weaponized code to run a remote system.
- Command and Control (C2): where we set a channel to a remote server where we can have control of the other system.
- Actions of Objectives: where the attacker now does what they wanted to do from the beginning, all the previous steps where only to gain access and do this.
This is the linear typical process, however there are another frameworks, for example the Mittre Framework, this is not linear but instead circular. Another one is the pre-ATT&CK which is form preventing an attack.
2. Malware
Malware is a software desing to infiltrate a system without their knowledge or consent, there are varios types.
2.1 Virus
It is malicious code run in the machine without the user's knowledge, the key part of a virus is that we as users take an action that allow the code to execute. There are 10 types of viruses:
- Boot sector: it is stored in the first sector of the hard drive and it is run everytime that we load the computer, this is very difficult to detect since it loads before the operative system.
- Macro: is a virus hidden in a virus, and when we open a file this are executed.
- Program viruses: it is an executable that seeks to hides inside a program so that everytime we load a program we load the virus too.
- Multipartite: it combines a boot sector virus with a program virus; it wants to load as boot and then everytime it can install itself in any program and reinstall everytime.
- Encrypted viruses: the viruses trying to be better they encrypt its contents to it be very difficult to detect them.
- Polymorphic virus: an advance encrypted virus that changes its decryption module in order to avoid detection even more.
- Metamorphic: a virus that rewrites itself before infecting a file.
- Armored virus: they have a layer of protection that allows them to protect themself to avoid being analyze.
- Hoax virus: it is a program that we are trying to make the user install, we do not have a virus unless we follow the instructions that are given.
2.2 Worms
It is very similar to a virus but it differs that it does not requires the user's action in order to execute, they can self replicate and spread without the user's action, for example take advantage of unpatch systems, they can disrupt network traffic by the replication they use; they distribute very fast.
2.3 Trojans
It is malicious software that it is disguised as something legit, it can even do what the user wanted but it will also execute something malicious, one subtype is Remote Access Trojan (RAT) it allows the attacker to have remote control of your machine and do whatever we want.
2.4 RansomWare
It is a malware that restricts the information in the systems, the encrypter ask for a payment in order to decrypt the files, the best approach is not to pay the ransom and also have updates backups; uses some vulnerabilities to encrypt the information.
2.5 Spyware
It is a software that gathers information about us without our consent, it goes through all the applications getting as much information of us as possible, it also could install keylogger or also take screenshot of access the webcam; a subtype of this is adware which wants to display ads to us according to want they discover we are interested in. The last one is grayware which is a software used to make something to the victim but not necessarily malicious but annoying (like jokes).
2.6 Rootkits
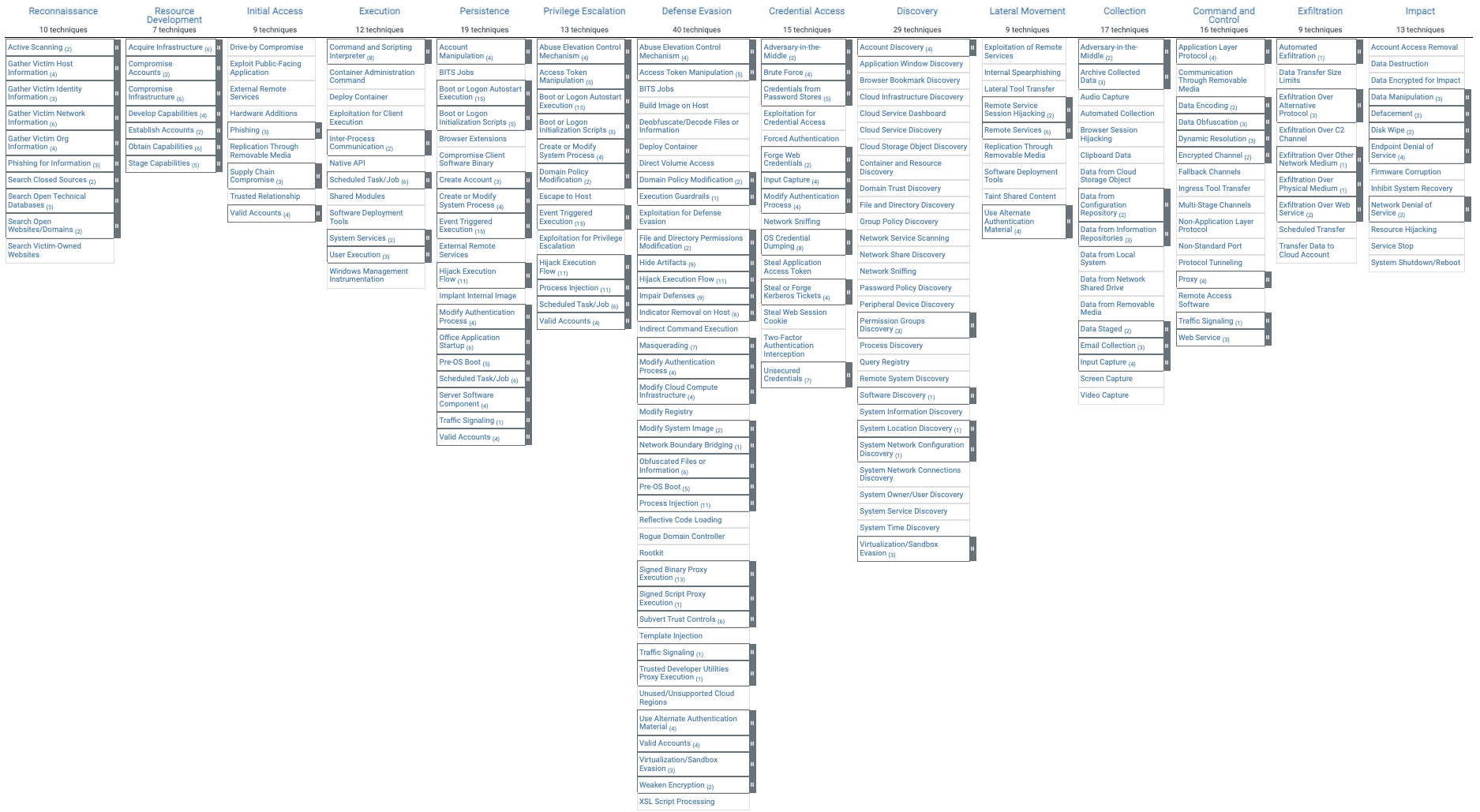
A software desing to gain admin controls to a system without being detected; with admin (root) priviliges they have access to the Ring 1 and the closer to Ring 0 or having access to the Ring 0 the best. They uses dll injection which is a malicious code inserted into a running process from a Windows machine by taking advantage of the Dynamic Link Library (DLL) which are loaded in runtime. It can also be done with driver manipulation because drivers have access to the kernel. This happens because of a shim is placed between it intercept the system calls. These are super powerfull and difficult to detect.
2.7 Spam
Activity that uses emails or similar to get unwanted messages, a lot of offers trying to sell something however it could be dangerous if it contains malware inside the message. They use open mail relays which is use an organization to send messages from a company sender domain. There is also spim which is spam but using messages like SMS or chat groups or similar instant messages.
3. Malware Infections
A threat vector is the way that an attacker get access to the system, for example an unpatch system. An attack vector is the method in which the attacker gets the access.
3.1 Common Delivery Methods
The most common are software, messages and media. Another method is watering hole which is our routine habits which we do everyday so could be websites which we need to use and could have malware. Even though if we have somethings we need to do and use, attackers could be use somethings very similar so we fall in the fake website for example, and place malware in that website.
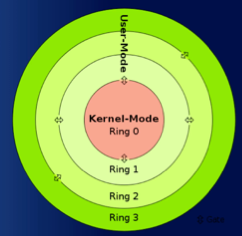
3.2 Bootnets and Zombies
These endpoints are use to distribute another attacks and even store their malicious content like child porn so that they don't get cough, they can even use these systems to make a Distributed Denial Of Service (DDOS); these are the functions of the zombies and bots in combination with the command and control (C2) servers; and the owner of the endpoint do not find out about this.
3.3 Active Interception and Privilege Escalation
This happens when a computer is placed between the sender and the receiver (men in the middle), the attacker can get credentials and even modify incoming traffic to embedded some malware in it. Now privilege escalation is when we use bugs to get access to resources that a normal user shouldn't have access to; this is order to get closer to the kernel.
3.4 Backdoors and Logic Bombs
Backdoors are use to bypass security authentication protocols, this was used originally to make updates to the systems, it used to be something common but they should not be use anymore; however a RAT (Remote Access Trojan) could be seen as a backdoor because we are bypassing the security protocols; another things are easter egg which is a joke, for example to he do a roll from Google, however this is a security concern because it does not go through security revisions. From here we get the logic bomb, in which the programmer or attacker puts some code that it is only executed when certain conditions are meet, for example delete all the database when I am not in the payroll; all these things should be avoided.
3.5 Symptoms of Infection
We can note that the computer behaves strange, the most common is that starts to run slower or displaying ads, another symptom is that the computer start crashing more frequently; also if the hard drive or file are not accessible anymore, basically when the computer starts to behaves strange. Also appearing or disappearing icons; all these is done to get persistent, also by getting double extension on files; or for example creating new files or folder, or changing the structure of the files; the final system is that we can not go to System Restore in Windows because the malware is trying to maintain the persistence, this can solved by loading the secure boot or boating externally and then removing the virus.
3.6 Removing Malware
- Scan the computer.
- Make sure we have a backup of all files since we can lose it all.
- What symptoms has the computer, because from this we can know what type of malware has the computer.
- Quarantine the system, to avoid it from communicating with other systems and infect them; we can make turning off the network card.
- Disable the System Restore (Windows) because we do not want the system to keep taking snapchats from the systems as we could restore some shot that is infected.
- Remediate the infected system; basically use some antivirus running the computer from a secure boot to avoid detection by the virus.
- Schedule automatic updates and scans, this is the preventing measure to prevent the malware to come back; make at least one scan per week.
- Enable System Restore and create a new restore point.
- Finally we will provide user with security awareness training so this doesn't happens in the future.
- If we suspect of a boot sector virus we need to reboot the computer from an external device. We could also disconnect the external drive and load it and scale it from another secure endpoint.
3.7 Preventing Malware
Viruses can be prevented by using a good antivirus, it is important to also updated the operative system constantly, we need to path the security breaches discovered. To detect:
- Viruses: we should use antivirus and keep our system updated as well as keeping firewalls and using encrypted websites.
- Worms, trojans, and ransomware: can be better detected by antivirus, ransomware can be detected in delivery by seeing suspicious programs.
- Spyware: there are special systems making sure no spyware and being deploy in our system, as well as having low level trust in the internet. We can detect it if we see a lot of ads of different browser homepage.
- Rootkits: scanners can be detect a rootkit before installing it, if it is already install it is very difficult to delete, we can try to detect it by running a scan from a external secure boot.
- Spam: we should verify our server to avoid that user use our servers, also removing email addresses from public places to avoid being subscribe to websites mail lists.
In summary we should always:
- Update our antivirus use in our computer, and check the computer weekly.
- Always keep our systems up to date.
- Educate our users of good internet security practices.
3.8 Malware Exploitation
An exploit technique is a method in which a malware infects a system, modern malware uses fileless techniques in order to avoid detection by signature-based malware. Here is how it works:
- Dropper or downloader: is by running light shell-code in our system which will download the rest of the malware, the idea is to trick the user to click or do something.
- Maintain access: the malware needs to download something like a RAT to persist access.
- Strengthen access: the malware tries to find more systems in the network, and get the permissions they need.
- Actions on objectives: now the attacker has the permission he need and will do what he wanted from the beginning.
- Concealment: the attacker will keep their access but they will also try to delete every evidence that they were ever in the system.
Now let examine every part individually:
- Dropper: its only purpose is to retrieve the rest of the malware from the internet; shell-code will refer to any code to get any type of external exploit; they can obfuscate or encrypt the payloads.
- Code Injection: it is a exploit technique that runs malicious code with the id from a legitimate process id; can be made by masquerading, DLL Injection, DLL Side-loading, or by Process Hollowing.
- Living Off the Land: exploit technique that uses system tools and packages to perform intrusions; the idea is to use your own tools agains you to make more difficult the detection and keep much longer inside the system.
4. Security Applications and Devices
The devices and applications that allows us to keep our systems secure, specially laptops.
4.1 Software Firewalls
They sit at the edge of our network and protect what comes in and out, however personal firewalls are host-based and should control what is coming in and out of our system. As they are software based we need to consider the OS:
- Windows: Windows Firewall, can be the normal our an advance firewall with more configuration.
- MacOS: the PF and IPFW, which is a built-in firewall. There is also a command option: pf.
- Linux:
iptables, which is a command line tool; also many anti-malware systems also offer firewalls and they need to be up to date since all software is vulnerable.
Some companies however like to have network-base firewalls and dedicated servers for firewalls for avoid using computer resources however we could use both firewalls to have two protection layers.
4.2 IDS - Intrusion Detection System
It is a software of device in a network that detects intrusions, there are two:
- HIDS (Host-based detection system): it is usually a software that logs everything that seems suspicious.
- NIDS (Network-based detection system): it is something that receives all the info from the devices.
Either of these two will search for signature-based intruders (bytes that may trigger an alert), also could be a policy-based detection, another one is anomaly-based where the systems knows patterns from our network and triggers anything suspicious.
The IDS only alert but do not stop, the IPS can stop the malicious activity. The HIDS are the logs used to recreate the actions taken by the attacker. There are types of alerts:
- True positives.
- True negatives.
- False positives.
- False negatives.
4.3 Pop-up Blockers
Most of the time these are use for malicious things however sometimes they can be for something legit, the problem with this is that attackers can embedded link to malicious websites. We could use ad-blockers but some websites do not allow the website if we have. Another solution could be content filters; but the best defense again these is to make sure the browser is up to date and disable them when is possible.
4.4 Data Loss Prevention (DLP)
It is uses to monitor the data from a company, and its transit to avoid losing it or being steal. These systems can be software or hardware:
- Endpoint DLP System: they are software based in the client and if they detect that someone is trying to transfer data they can stop it.
- Network DLP System: software or hardware based that monitor the data leaving the place and block data that should not go out.
- Storage DLP System: they inspect data at rest for anomalous activity.
- Cloud DLP System: cloud system that protects our systems in the cloud, usually offer by the cloud provider.
They all review all the movement of our data making sure none leaves without authorization.
4.5 Securing the BIOS
BIOS is the type of firmware (chip's software to control how to send input and output); most of computers they use Unified Extensible Firmware Interface (UEFI) they are almost the same. The BIOS tells how to read the hard-drive, loads the machine and how to use the rest of the components; to secure it we need:
- Flash the BIOS: making sure that the BIOS has the most updated version of the BIOS.
- Use a BIOS password: this will prevent anyone from changing the way that the computer loads, this should be a strong password.
- Configure the Boot Order: this so it can only be loaded from our main hard-drive for example.
- Disable the external ports that we do not use, for example we do not use serial ports anymore.
- Enable the secure boot option: this makes that the BIOS goes through additional steps when loaded and makes sure we load only secure versions.
4.6 Securing Storage Devices
We should always encrypt our files, in Windows we could use bit-locker or removable media controls that are technicals limitations implemented to limit the access to files (for example write and read privileges), we can also use a network attach storage (NAS) these systems uses RAID arrays to ensure availability to the networks, another one is Storage Area Network (SAN) which is a system implemented to perform block storage functions. Some tips:
- Always use data encryption.
- Use proper authentication.
- Log NAS access to the devices, so in case anything goes wrong we can go back and find the responsible.
4.7 Disk Encryption
It scrambles the data into unreadable information so no one can read it. Two type of encryption:
- Self-Encrypted Drive (SED): these are hardware-based drives that has embedded hardware that provides encryption.
- Software Encryption: for Mac we have FileVault, for Windows we have BitLocker. They both use the Trusted Platform Module (TPM) that keeps the key in the motherboard that makes the disk unreadable to anyone else even if removed if we do not have the key; they both use Advance Encryption Standard (AES) that may be 128 or 256 bits symmetric; they are good but makes our systems slower. In Windows we use IFF that is only encrypt some files.
- Hardware Security Module (HSM: uses for hardware encryption, that can be plugged for encryption but they are expensive.
4.8 Endpoint Analysis
An endpoint is any device used to connect to our network; we can list the next endpoint methods and devices used to protect our endpoint:
- Anti-virus: software capable of detecting malware and other types of attacks.
- Host-based IDS/IPS: monitors a computer for unexpected behavior, or changes in the file system.
- Endpoint Protection Platform (EPP): software agent and monitor system that performs multiple security task, DLP, Firewall and file encryption among other; it is more based in signature analysis; one example is SentinelOne.
- Endpoint Protection and Response (EDR): similar to the EPP however it relies more in behavior, it is to provide monitor the system and respond faster to a threat.
- User and Entity Behavior Analytics (UEBA): this is more of analyzing the data collected for suspicious activity so they are very depend on AI because they have to make a lot of analysis in a lot of data; some examples of these are Microsoft and Splunk User Behavior Analytics.
Many companies have started to combine multiple of these and selling them as a single combo.
5. Mobile Device Security
5.1 Securing Wireless Devices
We need to thing of two main things:
- WiFi: we should use the higher levels, today WPA2 that uses AES.
- Bluetooth: they share a link key to link their data, however some devices uses weaker security.
5.2 Mobile Malware
The first thing should be to have an anti-virus application in our phone, whether Android or iPhone, as well as making sure that the device is always up to date with software updates. If in Android we found a vulnerability Google has to path it and send it to the manufacturer and then he send it but this takes time, we should always install applications from the official store but the apps can also get to the store sometimes. We should also have the defenses up, so we need to be careful of where and what we browse. Some scams also come via SMS with link where if we click them we go to a malicious website. So we should:
- Do NOT jailbreak it.
- Do NOT use custom firmware or a custom ROM.
- Only load official apps from the official store.
- Always update the device's operating system.
5.3 SIM Cloning and ID Theft
SIM stands for Subscriber identify Module, which is a circuit that store the International Mobile Subscriber Identity (IMSI) and its related key, if someone can clone this number they can pretend to be us. SIM Cloning allows attackers to get access to our personal's data as we both get a copy of the data, however this is no longer easy since they are much much harder.
Attackers find another way in which they call the carrier and they transfer the SIM to another phone, this is very important because attackers wants this for 2-Step Authentication; this is ID Theft. To protect again this we should be careful where we put our phone number, another way avoid this is to get a Google Voice Number to use and nobody know our real number.
5.4 Bluetooth Attacks
- Bluejacking: it is sending unsoliciting messages to Bluetooth enable devices, here we send info.
- Bluesnarfing: it is unauthorized access to the information of a device via bluetooth, here we take.
In most cases most of the devices uses the default pairing key (0000), another way is that we could turn off bluetooth of make it no-visible.
5.5 Mobile Device Theft
We sure do a full disk encryption on our devices, as well as setting up tracking services to locate the phone, we should also have remote lock which is lock the phone when we know it's been lost, as well as remote wipe to delete all data from the lost device. Security of Apps We should only install applications from the official store, we should not jailbreak/rooting it. When ever we browse a website we should always use the SSL version of the website to use Transport Layer Security (TLS). Mobile Device Management are uses to create and enforce policies in the mobile devices (for an organization). We should be careful about the location access services. Geotagging is embedding the geolocation into a piece of data, for example into a photo as metadata, we need to be careful this because someone could get information about this.
5.6 Bring Your Own Device (BYOD)
If we allow users to bring their device to our organization this could have a lot of security issues for our organizations since we do not control anything related to the user's devices; however some companies like it since they do not have to buy computers or endpoint to the employees. Companies uses Storage Segmentation, that it is use to draw the line between data and work information. The employees will not let the company to install Mobile Device Management (MDM) in the phones; so we have a solution: Choose Your Own Device (CYOD) this gives the employee the choice of a couple of phones and then the company can install what the company needs, in this way both parts win. The MDM allow for example to disable the phone from connecting to public WiFi networks since they are not secure; the company has to take the decision of what they will use but not use the default.
5.7 Hardening Mobile Devices
The 10 best way to increase the security of a device:
- Keep the device updated to the latest software update.
- Install anti-virus.
- Train user in good security practices and what to use and not to use.
- Only install apps from the official stores.
- Do not root or jailbreak the device.
- Only use v2 SIM cards with the devices.
- Turn off all unnecessary wireless features.
- Turn on encryption for voice and data.
- Use strong password or biometrics for login.
- Don't allow BYOD in companies; rather CYOD.
6. Hardening
This is the act of configuring an operative system by removing unneeded apps and implementing policies to make it safe, the idea is to implement secure measures to avoid attackers; we are not guarranting than nothing bad will ever happen but making it more secure, minimizing the risk.
6.1 Unnecessary Applications
We should have Least Functionality that means we should only allow and have install only what the user really needs and uninstall all left. In large networks preventing unneeded applications is the best. For Windows we can use the System Center Configuration Management (SCCM).
6.2 Restricting Applications
We need to restrict what application can be run in which endpoint. This can be done by Application Allowlisting that means only what we allow to run special programs, on other hand is the Application Blocklisting where all apps will be allow to run except the ones in the list. Using allowlist is more secure but more difficult to control, but the blocklist has the problem that any variation of a program will run; they can both be centrally managed.
6.3 Trusted Operating System
Exist a certification for operation systems that meats some government requires, from Windows 7, MacOS X 10.6, FreeBSD and RedHat are consider trusted operating systems; they must patch continuously the systems.
6.4 Updates and Patches
A patch is a single problem-fixing piece of software, it is similar to Hotfix but this one does not require a reboot of the system where patches do; there are 5 categories of updates:
- Security Updates: software code to solve a vulnerability.
- Critical Update: software code that addresses for a critical problem but not related to security.
- Service Pack: it is a tested, cumulative grouping of patches and some minor changes; these are only released over the years.
- Windows Update: recommended updates that changes some visual changes for example.
- Driver Update: solves security issues from drivers or add new features for the drivers.
6.5 Patch Management
This is the planning, testing, implementing and auditing of software updates, his makes sure that a patch does not creates a new issue; for this we use Patches Management Systems and the process:
- Planning: procedures to determine if a patch needs to be deploy.
- Testing: we need to test it before deploying, we should have a lab or machine use to test and make sure that they work properly, after testing we can deploy.
- Implementing: if the test was successful we can deploy the update; we can control centrally manage updates instead of the Windows automatically, we can disable this last one.
- Auditing: after deploying we use this to make sure everything has gone well. Group Policies Also know as GPO (Group Policy Object); it is a set of rules or policies apply to user, to access we go to: cmd<gpedit. Each policy has a template for example for password requirements and etc. We can set a baseline to what is normal, for what we could consider normal network traffic, some breaches have been discover by unusual network activity.
6.6 File Systems and Hard Drives
The file system affects the way a system is secure; Windows system ca n be NTFS (New Technology File System) and Fat32; we can convert it from one to another one. In Linux can be ext4 and for MacOS is APFS. Hard drives will eventually fail but we can do:
- Remove temporary file by using Disk Clean Utilities.
- Do Periodic File System Checks.
- Defragment your drive every time to time.
- Back up our data.
- Use and practice restoration techniques; this include test the back ups.
7. Supply Chain Assessment
We can verify the components of a device we use in our networks, this allows to know what the components may have been expose to; we have to secure hardware, software, firmware, OS, and applications; however the importance of this depends on the company. Due Diligence is a legal principle that manifest that a products is in an optimal condition; for example if I buy something from a company do I know they will be in 5 years to give support to the product, will they be there to help us something goes wrong; this principle should be apply to suppliers, contractors and etc. A Trusted Foundry Program is a microprocessor manufacturing utility that is part of a validated supply chain, this has been created by the department of defense (DoD); we just need to know that the chips are secure. The Hardware Source Authenticity the source from where we get something affects its security, if possible we should go directly to the manufacture.
7.1 Root of Trust
A Hardware Root of Trust (ROT) this is a cryptographic module embedded used to scan the boot metrics and OS files to validate and sign files so that we can trusted; the objective is the Trusted Platform Module (TPM); we just need to remember that this TPM is the one that allow us so that every-time we load the system it loads securely. Another is a Hardware Security Module (HSM) that is a generating and storing cryptographic keys, it is software-based. The Anti-Tamper are methods that makes difficult for attackers to mess with these protective measures, we have the Field Programmable Gate Array (FPGA) and a Physically Unclonable Function (PUF) that prevents attackers from modifying these things.
7.2 Trusted Firmware
A firmware exploit gives the attacker the highest level of privilege; we need to understand the following:
- UEFI (Unified Extensible Firmware Interface): offers support for 64-bit CPU operations at boot.
- Secure Boot: prevents unwanted processes from loading.
- Measured Boot: gather metrics to validate the boot process in an attestation report.
- Attestations: a claim that the data presented is digitally valid and signed using a TMP's private key.
- eFUSE: a means for software or firmware that persistently alters a transistor of a chip. Here uses a one time programming that makes sure that the code can not be rewritten.
- Trusted Firmware Update: firmware updated that is digitally sign so we know it is secure.
- Self-Encrypted Drives: it does the encryption and decryption automatically by the firmware and a hardware level.
7.3 Secure Processing
It is a mechanism to ensure the confidentiality, integrity and availability of a software code. We have:
- Processor Security Extensions: Low-level CPU that enable secure processing, they
are divided by:
- AMD:
- Secure Memory Encryption (SME).
- Secure Encrypted Virtualization (SEV).
- Intel:
- Trusted Execution Technology (TXT).
- Software Guard Extensions (SGX).
- AMD:
- Trusted Execution: The CPU's security extensions invokes a TMP and Secure Boot to ensure that a trusted security system is the one running.
- Secure Enclave: extension that allows a trusted process to create an encrypted container for sensitive data.
- Atomic Execution: they are some operations that can only be run once or not at all, this can be safe against buffer-overflow attacks.
- Bus Encryption: data that is encrypted by an applications prior to being places on the data bus; this will make sure that the data send via network or the bus, is trusted, this will work only if on the other side the data is also trusted.
8. Virtualization
A system virtual machine is an idea to create an entire platform, mean while a processor virtual machine is intended to only run a program to test something specific.
8.1 Hypervisors
Manages the distribution of the physical resources to the virtual machine, there are two: Type I: also know as bare metal, runs directly on the host and works as an operation system itself; they tend to be more efficient. Type II: runs over an operation system. Container-based: the OS kernel is shared for all but the user space is unique, this allows to run distributed applications and makes these more efficient; for example Docker.
8.2 Threats to VM
VM are separated from other VM:
- VM Escape: happens when an attacker breaks from the isolated part and get to the space of another virtual machine.
- Data Remnants: happens when we deescalate a server and the files that were in it are not deleted and an attacker gets it.
- Privilege Escalation: happens when an user gets access to the permissions from the kernel.
- Live Migrations: happens when we migrate a VM and an attacker gets in between of the transfer and therefore happens a Man-In-The-Middle.
- When the attacker get to exploit the main OS that host all the VMs and therefore they all are at risk.
8.3 Securing VMs
The hypervisor need to always be updated; we should always limit the connectivity between the virtual machine and the hypervisor; we also need to remove all unnecessary pieces of software preinstalled; also using proper patch management and also virtualization sprawl to keep track of all the machines created, the user and permissions assigned, also not having shared folder so that the machines are isolated, and finally encrypting our virtual machines.
9. Application Security
9.1 Web Browser
We should always install the latest patches for browsers, but we should never be the first one to change to a new browser version since this can have bugs and be unsecure. We should do:
- Implement good policies for administrative control.
- Train the users.
- Use proxies and content filters.
- Prevent malicious code from being loaded, for example prevent some JavaScript.
9.2 Concerns We Should Have
- Cookies are sued to store client information, habits and credentials; there are tracking cookies uses by spyware to get what we use and do, session cookies are to keep track of users and preferences, as well as for tracking the users. People do not like this so they use service tracking services so that we can block cookies. If we want to protect them we need to to use the Secure Attribute on the Cookie because SSL/TLS do not protect the cookies's confidentiality.
- Locally Shared Object (LSO) they are store in the Windows system in AppData folder, they should no longer be used.
- Add-Ons that are small extensions and plugins, we need to be sure about what code we install and what code don't install.
- Advanced Security Options, here we can change to only use SSL/TLS when browsing.
9.3 Securing Applications
We should use passwords to protect files from viewing or even being modifying; we should check our MACROS setting and disable them always. Also we can use digital certificates to only show information to those with authorization. The User Account Control (UAC) allows us to get an user in a controlled access to prevent unauthorized access, so the user runs like a normal user instead or an admin user.
10. Software Development
The most common way is SDLC (Software Development Life Cycle) that handles all the steps of the software development like a waterfall to go to a new step after we complete a previous one, the phases are:
- Planning and Analysis: here is where we pass from an idea to start planning.
- Software/System Design: where we make the diagrams.
- Implementation: programmers will make all the code require for the program.
- Testing: we will test it using different methodologies.
- Integration: we make sure all parts can work together, like servers and so.
- Deployment: moving the application into the production environment.
- Maintenance: we do bug fixes, patches and so, and education the users on how to use it. We need to have in mind version control and configuration management, usually with numbers (1.1).
The problem with this is that it is slow, so an alternative to be able to add features during development is using Agile methodology, and working with sprints. DevOps are the people who work as software developers and IT as well so he can be that bridge and get the app live faster.
10.1 SDLC Principles
Developers should always remember confidentiality, integrity and availability. To best protect are our applications we should make sure to use secure coding practices instead of implementing many security extra layers. When we program we should keep in mind:
- Least privilege: for example that our program does not need admin rights.
- Defense in Depth: making it secure in all layers.
- Never Trust User Input: always make sure to validate the user input.
- Minimize Attack Surface.
- Create Secure Defaults: making our default configuration the most secure one.
- Authenticity and Integrity: using code signing to verify our code has not been change during the download process.
- Fail Securely: use error handling for exceptions instead or crashing.
- Fix Security Issues: if we discover a vulnerability then patch ASAP.
- Rely only on Trusted SDKs: they all must come from trusted sources to ensure no malicious code has been added.
10.2 Testing Methods
- System Testing:
- Black-box Testing: the tester is not given any information related to the system and it is my responsibility to discover everything.
- White-box Testing: the tester is given all the details of the program, like source code and diagrams.
- Gray-box Testing: the tester is given some information about the program but conducts the test like if he has no info, for example if he has the list of users but makes the test as normal.
- Structure Exception Handling (SEH): provides a control over what the app should do when a runtime error occurs. From these we can discover if the programmers did input validation, and this can be an entry point for an attacker.
- Static Analysis: is when we analyze the source code by reading it manually or with automatic tools and we try to find some errors.
- Dynamic Analysis: is the testing during the run of the program, common is Fuzzing where we inject random data attempting to find vulnerabilities in the system by input.
10.3 Software Vulnerabilities and Exploits
- Backdoors: it is software code that it is there by developers in order to bypass authentication methods, backdoors should never be used by programmers; however some attacker may created.
- Directory Traversal: method of accessing unauthorized directories by moving through the directory structure.
- Arbitrary Code Execution (ARC): when an attacker is able to run commands on a victim computer but here the person has to be present in the physical space.
- Remote Code Execution (RCE): similar to ARC but here the attacker can runs the commands remotely.
- Zero Day: when someone discover a totally unknown vulnerability to the system.
10.4 Buffer Overflows
Occurs when a process stores data outside the memory of the program; 85% of the breaches were caused by an overflow attack. The problem with this is that we are messing with the stack and the memory of other programs, being able to even replace the code that the program is supposed to run. They try to rewrite the return address of the code so it goes somewhere else, this is call the Smash the Stack, so the program runs until finds our malicious code. One of the mitigating is Address Space Layout Randomization so the return addresses are randomized so the attacker can not know where to overflow the stack.
10.5 XSS and XSRF
- Cross-Site Scripting (XSS): when the attacker embeds malicious script code the a trusted website, there are 3 types; to prevent it we should always use input validation and disabling scripting things: ◦ Stores/persistent: attempt to get data provided by the attacker to be saved in the website. ◦ Reflected. ◦ DOM-Bases: attempt to exploit the victim’s web browser.
- Cross-Site Request Forgery (XSRF/CSRF): when an attacker forces an user to execute actions on a web server that they are already authenticated, to make look requests as if they came from us. To prevent these we should use encryption, tokens, XML File scanning and checking cookies twice to verify the integrity of these ones.
10.6 SQL Injection
Inserting SQL queries via input data forms that are send to the server from a client application, the most commons injections are: SQL, HTML, XML and LDAP injections. We can prevent it by using input validation and least privilege principle when accessing the database, and do NOT trust input.
10.7 XML Vulnerabilities
This is a markup language, we should always use encryption and input validation, to prevent it we must use input validation; this manipulates any part of the XML markup language. The types of attacks are:
- XML Bomb (Billion Laughs Attacks): encodes entities that expands the size and consuming resource of the memory on a host to make it crash potentially.
- XML External Entity (XXE): embeds a request for a local resource.
10.8 Race Conditions
Something from parallel programming when it fails by the race conditions by accessing a variable at the same time by threats; the vulnerability is when we remove the relationships from the pointer to point it to something malicious. They can be used agains files and databases not only OS. The Time of Check/Time of Usage is when it is a change between when the app checked the resource and when the app used the resource, so if the attacker figured out the time when the app checked the resource and when the app used it; for example if we buy something in Amazon that it is no longer in stock. To prevent it we can:
- Not running things in a sequence.
- Implement locking mechanism to exclusive access.
10.9 Design Vulnerabilities
- Insecure Components: any code that is used or invoked outside the main program, for
example:
- Code reuse.
- Third-party Library.
- Software Development Kits (SDK): if there is a vulnerability from someone else then we are bringing it to our systems.
- Insufficient Logging and Monitoring: if we do not have this we do not have a way to detect thing; with this we can know who, what, when, where and how something happened.
- Weak of Default Configurations: this happens a lot in the real life, and also that people run things with root permissions or they use the defaults configurations that are weak. We should use secure scripts to install things and make it secure from installation.
11. OSI Model
The 7 layers, can be remember by Please Do Not Throw Sausage Pizza Away:
- Physical: the cables and radio waves used to transport the layers in bits.
- Data Link: how connections are established and maintained, like MAC Addresses.
- Network: routing and switching information, the frame for layers 2 become packets; use routers.
- Transport: TCP or UDP for transmitting packages; they are segments (TCP) or datagrams (UDP).
- Session: manages the establishment, synchronization and termination of the session.
- Presentation: translates the information that both sender and recipients will understand, like for example using UTF-8.
- Application: where messages are created and sent from; for example HTTP, SMPT and FTP.
11.1 Switches
They operate at level 2, they are the combination of hubs and bridges, each port of a switch act as both of them. They are vulnerable to:
- MAC Flooding: overwhelm the limited memory that the system has for MAC Address in the port.
- MAC Spoofing: the attacker mask their own MAC Address to pretend to be another device when for example the MAC Address is blocked; this can be combine with other protocols using MAC.
- Physical Tampering: when the attacker gets access to the switch because they can be reconfigure on place.
11.2 Routers
They work at level 3 and are used to connect two networks or more, they use IP Addresses to determined the route. The default configurations of these tend to be very weak and things like firewalls are usually used to protect the network.
11.3 Network Zones
Most of the network are usually map in LAN, WAN and DMZ; we should route our traffic through a VPN when accessing the internet. The De-Militarized Zone (DMZ) is to control the access to servers that have public access. Not all devices require the same level of protection, some may need more or less and for this we can use sub-zones and extranet which is a special DMZ but it is not publicly accessible. Intranet is a special internet for our only company.
11.4 Jumpbox
Internet-facing host or devices are the devices that accept traffic from all the internet, even if they did not request it. The DMZ is isolated from the rest of our network, this can accept request from the internet but it is separated from the rest of the internet and if someone scans our network they will not see everything in our network; anything that someone from the internet may need should be in our DMZ. A jumpbox is a server that can communicate with the DMZ from the internal network, it is like our bridge but this requires heavy security configurations and programs; they can even be VM. A jumpbox is also good idea for systems where we do not have much control.
11.5 Network Access Control
NAC is used to protect the network from know and unknown devices, it scans the devices connected and then checks anything that could make our network unsafe, if the device fails it is placed in quarantine and then receive any update that it may need, they can have persistent and non-persistent networks, this last one is more for networks where people use their own devices, for example connecting to a public internet place. One of the standards used is the IEEE 802.1x.
11.6 VLANs
- Switch Spoofing: it pretends to be a switch and negotiates a trunk link to break our of the VLAN.
- Double Tagging: adds and outer and inner VLAN tag to break out of our VLAN.
11.7 Subnetting
Creates logical subnetworks using IP Addresses manipulation; it makes our network more efficient; and we can also implement different policies for each subnetwork as well as monitoring the network.
11.8 Network Address Translation
NAT is changing the IP Address of a device while it is transfer, this can help us for example hide the devices in our network. The private IP addresses ranges are:
- Class A:
10.x.x.x. - Class B:
172.16.x.xto172.31.x.x. - Class C:
192.168.x.x.
11.9 Telephony
- War Dialing: when the attacker digits random numbers to see if someone answer it, to protect this (vulnerability from modem) is to use the callback feature. The best practice is to eliminate modems and use SSH instead, and keep our number secrets.
- Public Branch Exchange (PBX): the internal phone system used in our organization, attackers use this to make long distance calls for free, for this we should remove any remote access points.
- Voice Over Internet Protocol (VOIP): we should not place this VOIP in the same subnet as our computers, this phones are connect by their own IP phone and this connects to the gateway to make the connection work; this devices should always be updated and have good encryption.
- Quality of Service (QoS): the availability is required since VOIP required a lot of bandwidth and have a good availability.
12. Perimeter Security
12.1 Firewalls
They are use to protect one network from another; they can be:
- Software.
- Hardware: like another router.
- Embedded: they are one piece of the large device.
They do:
- Packet Filtering: accepts or rejects packets based on some rules; they can be:
- Stateless: filters based on ports and IP Addresses.
- Stateful: tracks the request leaving the network.
- NAT Filtering: filters based on the connection (TCP or UDP).
- Application-Layer Gateway: conducts in-depth inspection in each packet to determine any threat, they operate at layer 7.
- Circuit-Level Gateway: operates at Layer-2, the Session Layer.
- MAC Filtering.
- Explicit Allow: the rule allows something to happen.
- Explicit Deny: traffic should not allow something that matches the rules.
- Implicit Deny: traffic is deny because it does not find any matching rule.
Most usually the firewalls used to work on the Layer-3 however some more moderns work on more layers, like Layers (2, 4, 7).
12.2 Web Application Firewall (WAF)
It is install in a server and controls web applications, they protect agains cross-site scripting, SQL Injection and similar.
12.3 Proxy Servers
Acts as a Middle-Man, so the company can log everything requested, types are:
- IP Proxy: use to secure the network maintaining the machines IP address anonymous.
- Caching Proxy: to serve client requests without accessing the server every-time.
- Internet Content Filter: used in organization to filter some websites or email servers.
- Web Security Gateway: a go-between device that scans for viruses to filter anything unwanted.
12.4 Honeypots & Honeynets
Use to attack and attracts attackers, a honeypot can be a computer, file or anything similar; a honeynet is a group of computers and servers; this is usually used by computer research to learn about the attackers.
12.5 Data Loss Prevention
Are systems to protect data by inspecting data leaving the network, they can also be know as Information Leak Protection (ILP), or Extrusion Prevention Systems (EPS). This protects data leaks.
12.6 NIDS & NIPS
Network Intrusion Detection System (NIDS) is a device that attempts to detect logs and alerts on the network, usually are placed behind or in front of the firewall; usually they are use to all the traffic; they can not stop an attack, they only log. A Network Intrusion Prevention System (NIPS) is used to remove and retain or redirect any malicious traffic; we should configure these very well in order to not create a lot of false positive, we need to decide if they fail open or closed so for when they fail.
12.7 Unified Threat Management
Also call as UTM, relaying on a single firewall is not enough, is the combination of devices and technologies to protect the network; it is just see all the devices as one device, so the administrators can use a graphic interface instead of a command line. The Next Generation Firewall (NGFW) is a all-in-one device to protect the network.
13. Cloud Security
Cloud computing relies heavily in virtualization. Hyperconvergence allows providers to fully integrate the storage, network and server, they also offer Virtual Desktop Infrastructure (VDI) which allows to handle much better things with virtual machines for even endusers. We have secure enclaves and secure volumes.
13.1 Cloud Types
Four types of cloud:
- Public: a service provider makes resources available to the users in the internet.
- Private: a company creates its own cloud environment that only uses internal resources, when security is more important than cost.
- Hybrid: strict rules should be applied.
- Community: the cost and resources are shared among organizations, this involves many security challenges since every network may involve their own risk.
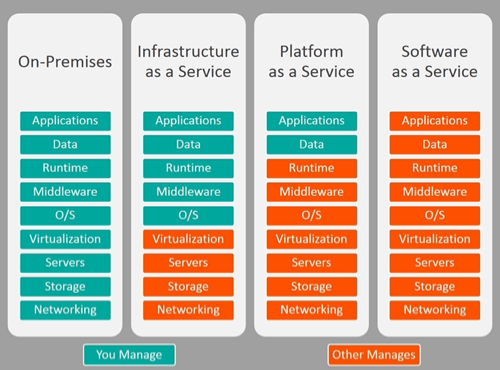
13.2 Cloud As A Service
Four types:
- Software As A Service (SAAS): we are provided a complete solution; software, hardware and anything required, so the users can access the tool from the browser.
- Infrastructure As A Service (IAAS): we have access to all the resources and we configure them as we want, but we do not worry for long-term tasks.
- Platform As A Service (PAAS): the provider will give us the specific hardware and service.
- Security As A Service (SAAS): when a company outsources the security responsibilities to another company. This can even reduce cost since we don't need the security 24/7; however we lose control over our data. We can also have sandboxing in which we can test any possible malware, and see the effects of this malware.
14 Cloud Security
We need to consider that we may have our resources in a space where another company has their content and they may not have the same level of security. We should always make sure that the resources have the latest software updates. We should use strong password and similar things; and the data should always be encrypted.
14.1 Defending Servers
- File Servers: any computer may access this server in the world, we should make sure that it has logging tools and strong encryption.
- Email Servers: at the minimum we have 3 open ports but are usually more; we should have spam filtering and quarantine policies as well as strong policies configuration.
- Web Servers: they must be in the DMZ and have firewall and patch.
- FTP Server: stores files to distribute among the web, for example to distribute an app, they must have a secure connection to transfer any files.
- Domain Controller: aka Active Directory in Windows; this is usually a target for hackers, one common attack is the Golden Ticket, they have strong configuration, with the latest software and in a secure environment in the network.
14.2 Cloud-Based Infrastructure
We need some knowledge to configure the cloud as strong as our local network; we can consider Virtual Private Cloud (VPC), it is consider a private network with a single cloud consumer within a public cloud; as a consumer it is responsibility to configure the IP Address. With On-premises solutions we have the benefit of having physical access, but if it fails it is our total responsibility; which cloud we do not need to worry about fails but we don't have physical access to it. The cloud has the benefit of many many resources to use in AI and Machine Learning. We also should be careful of vendor lock for in the future we want to move to another provider.
14.3 CASB
Cloud Access Security Broker (CASB) it is a management software designed to mediate access to cloud services by across all the users; this makes sure that our device is connected to the correct device. So we have:
- Single sign-on.
- Malware and rogue device detection.
- Monitor/audit user activity.
- Mitigate data exfiltration.
We need to consider Forward-Proxy but this is vulnerable to Proxy-Bypass, so we can also consider Reverse Proxy but this only works if the application support Reverse Proxy. We can also use API to indicate which users allow access and deny to. APIs allow integration between many services. We can use curl to test APIs.
14.4 Function As A Service and Serverless
FAAS is a service that allows to run things without having our own server. We can just write some code and run it in this enviroment. Everything here is a function or microservice and so it should only do one thing; for example Netflix. This eliminates the need to managed the server and all its requirements; we can even set it to only be run and charged for us the only time that we need/use.
We do not need to patch the server, no file system monitoring and is cheaper. Our job here is only to ensure that the clients accessing the service have not been compromised, that our code is secure, that the credential are safe. One of the problems is that we trust the service provider that they will surely do the job correctly, we won't have control over what they do. It is all about automation/fast.
14.5 Cloud Threats
Most of the threats are from user's identity. Here is a list:
- API: we should always:
- Use it over a secure (HTTPS) channels.
- Server-Side Validation.
- Error-Messages: what clues are we given the user, without giving too much details.
- Prevent DDOS.
- Improper Key Management: we need to:
- Make sure of being use secure authentication and authorization.
- DO NOT hardcode or embed keys into the source code.
- Generates new keys when going to prod.
- Delete unneeded code.
- Insufficient Logging and Monitoring:
- The logs must be copy to a long-term retention place, to prevent losing them.
- Unprotected Storage: they usually are call buckets (AWS) or blobs (Azure):
- Access control should be very strict, and avoid misconfiguration and permissions.
- Incorrect Origin Settings: use the Cross Origin Resource Sharing (CORS) Policy, that tell the domain to trust things from some specific domains; avoid XSS here.
15. Automation
15.1 Workflow Orchestration
It is the automation of multiple steps; what do I need to get from A to B. Orchestration is the automation of the automations. There a three types:
- Resource Orchestration: to things like cloud, like new VM.
- Workload Orchestration: managing apps and things that work together.
- Service Orchestration: working on the services itself.
15.2 Continuous Integration (CI) / Continuous Deployment (CD)
This tries to speed ups the process of software development to avoid all the steps that slows down. So in a shared environment everyone develop, test and deploys the code. With this we can test and commit multiple updates peer day. Continuous Delivery is always testing everything new, not necessarily install it at once but yes have it ready. Delivery is testing to get it ready and Deployment is to automate testing in order to get it ready production.
15.3 DevSecOps
This makes the same as DevOps but also uses the part of the security measures required; this solves a lot of problems. So we put security and put it right at the beginning of the development process instead of the last as usually happens; we also test during and after the development; and we also automate compliance checks (speed up using scripts and similar).
15.4 Infrastructure As Code (IAC)
This allows us to use script approaches to speed us process, has three areas:
- Templates.
- Scripts.
- Policies.
All these makes our organization safer. Some people want to have their own Snowflake Systems which are users who wants to make the things their way, even though their techniques may be slower. Also a proper IaC should always have the same output, and because of this we want to delete these snowflake systems; eliminate the Snowflake Systems, so we all have the same security.
15.5 Machine Learning
- Artificial Intelligence: are machines that simulate to think by themself.
- Machine Learning: a set of AI where we develop strategies for solving task by given a labeled
dataset so the machine can learn. The problem is that if we do not train it correctly then we could
train it to make wrong things like for example being racist, so they are as good as the dataset given;
usually the most typical examples of ML
- Neural Network: they try to adjust the system to become better every time.
- Deep Learning: almost the same as ML but without further instructions, the model will take more decisions by itself.
16. Network Attacks
16.1 Ports and Protocols
An inbound port is when we are listening for a connection and connect to it; an outbound is open by my
computer when I want to connect to a server. Ports can be [0, 65535] divided in:
- Well-Know Ports: 0-1023, assign no know services like SSH, HTTP.
- Registered Ports: 1024-49151 assign to proprietary protocols, like SQL.
- Dynamic or Private Port: 49152-65535: can be used in any application or any service that needs a temporary service.
16.2 Most Important Ports
- 21/FTP - TCP
- 22/SSH, SCP, SFTP - TCP/UDP
- 23/Telnet - TCP/UDP: this is unencrypted and should not be used.
- 25/SMTP - TCP: Simple Mail Transfer Protocol.
- 53/DNS - TCP/UDP: resolves hostnames.
- 69/TFTP - UDP: get or put a file in a remote host; most secure ways to transfer.
- 80/HTTP - TCP: web pages unencrypted.
- 88/Kerberos - TCP/UDP.
- 110/POP3 - TCP: received mail from a mail server.
- 119/NNTP - TCP.
- 135/RPC/DCOM-scm - TCP/UDP
- 137-139/NetBIOS - TCP/UDP
- 143/IMAP - TCP
- 161/SNMP - UDP: monitor network devices.
- 162/SNMPTRAP - TCP/UDP
- 389/LDAP - TCP/UDP: active directories.
- 443/HTTPS - TCP: uses SSL/TLS.
- 445/SMB - TCP: shared access to files in a network.
- 465/587 / SMPT with SSL/TLS - TCP.
- 514/Syslog - UDP.
- 636/LDAP with SSL/TLS - TCP/UDP.
- 860/iSCSI - TCP: linking data.
- 989/990 / FTPS - TCP: file transfer protocols encrypted.
- 993/IMAP4 with SSL/TLS.
- 995/POP3 using SSL/TLS - TCP.
- 1433/MS-SQL-S - TCP.
- 1645/1646 / RADIUS (alternative) - UDP.
- 1701/L2TP - UDP: tunnel protocol for VPN.
- 1723/PPTP - TCP/UDP.
- 1812/1813 / RADIUS (defaults) - UDP.
- 3225/FCIP - UDP.
- 3260/iSCSI Target - TCP: listens for iSCSI connections.
- 3389/RDP - TCP/UDP: Remote Desktop Protocol graphic.
- 3868/Diameter - TCP: replacement for RADIUS.
- 6514/Syslog over TLS - TCP.
16.3 Unnecessary Ports
We do not have and need to keep all the ports open, any unnecessary port is any port that we do not have strictly open right now. To stop we can do it from the OS; graphically or from command line; or we can also block them from the Firewall.
16.4 Denial of Service
Any attack that wants to make a computer or server unavailable; types are:
- Flood Attack: sending more request than the server can handle. There are many
types:
- Ping Flood: doing it by sending too many ping (ICMP) request.
- Smurf Attack: like a ping but sending it to the broadcast channel.
- Fraggle Attack: directs the traffic to the port 7 (UDP), this is an old vulnerability.
- SYN Flood: the attacker initiates many HTTPS request but never establishes the handshake, so the server reserver resources for this client but the client never arrived; flood guards can be installed, or we can set timeouts to dismiss these unused connections.
- XMAS Attack: a special package send to cause the device to crash because they don't know how to handle it.
- Ping of Death: sends an oversize and malformed package so the computer crash.
- Teardrop Attack: breaks the packages so they can not be rebuild in the other side and so the system crashes.
- Permanent Denial of Service: exploits a security flaw to permanently break a networking device by reflashing the firmware.
- Fork Bomb: creates a large processes to use up the available processing power of the computer.
16.5 Distributed Denial Of Service (DDOS)
Like when we use zombies computers for sending many request from different places. To stop them and prevent them we can use:
- Blackholing or Sinkholing: identifies malicious IP.
- IPS can prevent these is a small network.
- Have an elastic network.
16.6 Spoofing
Occurs when an attacker hides his identify by changing his data; anything the identifies an user; for example changing our MAC Address, or changing the IP Address.
16.7 Hijacking
Exploitation of a computer session to try to get access to data, service or any other resource; there are different types:
- Session Theft: attacker guess the session ID and then take the already enabled session.
- TCP/IP: takes the TCP session between the computer if they can guess the next package number.
- Blind Hijacking.
- Clickjacking: uses techniques to make the user click something to take the user somewhere else.
- Man-In-The-Middle.
- Man-In-The-Browser: like the man in the middle but instead of being in the computer it is located in the browser.
- On-Path: is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other.
- ARP Poisoning: also known as ARP Spoofing, is a type of cyber attack carried out over a Local Area Network (LAN) that involves sending malicious ARP packets to a default gateway on a LAN to change the pairings in its IP to MAC address table.
- Watering Hole: malware placed in a website.
- XSS: targets the victim and get another client to execute some code.
16.8 Replay Attacks
When valid data transmitted is malicious or delayed; for example replaying a connection made for the victim with his bank. Can be prevented using Multi-Factor Authentication; it is very used in Wireless Authentication.
16.9 Transitive Attacks
The idea of network trusting network, that if we trust one network and the other one trust other one so someone from the third network will be trusted by us too.
16.10 DNS Attacks
Different types:
- DNS Poisoning: when the name resolution information is modified in the DNS server's cache.
- Unauthorized Zone Transfer: attacker request replication of the DNS server.
- Altered Hosts File: modifying the file that has information about little DNS in our computer; this file should only be set on read-only.
- Pharming: traffic is redirected to the attacker's website.
- Domain Name Kiting: keeping the domains in the limbo before buying them. Address Resolution Protocol (ARP) Poisoning When an IP is resolved when translated the victim gets the attacker's or another malicious IP.
17. Securing Network
17.1 Securing Network Devices
The main vulnerability is the default accounts, we must always change these default users. We also be careful of privilege escalation, since the if we do no update the systems this can happen by exploiting bugs, this can happen horizontally or vertically. Another one are the backdoors which is a way of bypassing the authentication methods, this could be coming by software or hardware.
17.2 Securing Network Media
Electromagnetic interference (EMI) this is something that can affect the physical systems because of all the signals that have been sent, to protect this we should use shield on the cables, for example using STP. Other one is Radio Frequency Interference (RFI) this is cause by radio waves. Other one is crosstalk happens when se have two cables on top of each other. Data Emanation is when inside our cables generates signals trying to escape and if someone captures it, then someone can try to capture it. All these problems can be prevented by using Protected Distribution Systems (PDS), which is a lock to every network crossing but this is only necessary for governments or military.
17.3 Securing WiFi Devices
First we should not use default account in the wireless configurations account, other one is the Service Set Identifier (SSID), we should disable the broadcast so the users must know first the name of the network. The Rogue Access Point is an unauthorized Wireless Router that may be very weak and easy to break so should not be used and implement filters in the network. Another one is the Evil Twin, is a rogue replicating the same SSID to make users think they are connecting to the real network when they are not, this one can not be stop but preventing by making users use a VPN.
17.4 Wireless Encryption
They use Pre-Shared Key, which is when the client and point uses the same key to decrypt. The types of encryption:
- Wired Equivalent Privacy (WEP): the first protocol with 24-bit encryption.
- WiFi Protected Access (WPA): replaces WEP, uses RC4 for encryption, and ensure data integrity.
- WPA2: now uses a 128-bit encryption and solves some fails from the original one; CCMP and AES.
- WiFi Protected Setup: relays on an 8 digits code but break in two, should be disable.
- VPN: we should always use VPN, never trust any network.
17.5 Wireless Access Point
We should control in which direction the signal is being sent (not omnidirectional) but using unidirectional, and so use directional antennas and what type of frequency are we sending. We could be victims of Jamming (when the radio frequency is getting interference). More advance is Access Point Isolation that segments every client connected and prevent from connecting to others.
17.6 Wireless Attacks
War Driving is searching wireless network available hunting for network, is not to attack your network but attack other network using yours. War Chalking which is sharing the info with other people, this is more done digitally where the hackers shared their finds. IV Attacks is when an attacker observes the different keys shared and finds a mathematical relationship between them. WiFi Disassociation Attack, it targets a client and then captures the handshake that the client send when tries to connect again. Brute Force Attack is trying all the possible combinations.
17.7 WPA3
It is the WiFi Protected Access 3, designed to solve the fails of WPA2, we should be using it; this has 192-bits encryption when enterprise mode, in this mode is for business case that uses AES-256 and also a hash for integrity checking. In personal mode it uses CCMP-128 as the minimum encryption required. The big change is the removal of the Pre-Shared Key (PSX) exchange, now this is not possible to capture, we uses a Simultaneous Authentication of Equals (SAE), uses Perfect Forward Secrecy to protect the dat in long-term, so even if someone captures it, the persona can not use it:
- The AP and the client use a public key to generate a pair of keys.
- The AP and the client exchange a one-time use session key using a secure algorithm to encrypt the tunnel, for example using Diffie-Hellman.
- The AP sends the client messages and encrypts them using the session key created in step 2.
- The client will decrypt the message using the key from step 2.
- The process is repeated over and over. The keys changes a lot so if someone captures them, it does not matter since they will change very soon in the same session.
17.8 Other Wireless technologies
Not only WiFi is vulnerable but also Bluetooth, this was Bluejacking (sending unsolicited messages to devices), Bluesnarfing (takes information from devices); and change the default password. We also have RFID and is very used for authentication for doors or cars for example; it can operate from 10cm-200meters, and it is vulnerable to malicious captures; so Near Field Communication (NFC) was invented, they can also be capture and reuse but they need to be 4cm close. All these technologies are vulnerable to capture and jamming so when should encrypt the transmission.
18. Physical Security
18.1 Surveillance
We usually use CCTV. Also PTZ (Pan Tilt Zoom) which are the cameras that can be moved with a joystick. Another system is the infrared and ultrasonic systems. The placement is really important.
18.2 Door Locks
The locks can be the last part of security, but they can be picked. Instead of these we should use keys, pins, wireless signals or biometrics. And even electronic access systems like RFID. Another thing is Mantrap, that is an area that holds people until their identification can be verified.
18.3 Biometrics Reader
Here we focus on "something you are", like fingerprints or the distance of factions in our face; we need to focus on the False Acceptance Rate (FAR) and the False Rejection Rate (FRR). To solve both of these we need to find a balance so they be equal, this is call Crossover Error Rate (CER) and the two rate overlaps.
19. Facilities Security
19.1 Fire Suppression
The rules and implementation made to protect agains fires, three types:
- Handheld: the extinguishers, types:
- A (water based)
- B (flammable liquids and gases)
- C (fire involving live electrical)
- D (combustable metals or combustible metals like laptops batteries)
- K (cooking oil)
- Sprinklers: can be wet or dry pipe, wet is when there is already water in it ready to be used, a dry one does not have the water and only pushes it when needed. There is also a pre-action that it is set up for heat or smoke, does not need fire to activate. Instead of use this for server rooms we use Clean Agent System which releases gases. Humidity should always be 40%.
19.2 Shielding
We should use STP cables that are shielded cables, we need to protect shield on all cables and generators to avoid signals interference. TEMPEST is a certification required for the US Government to make sure the information can not leak by signals interference.
19.3 Vehicular Vulnerabilities
The vehicles connect over a Controlled Area Network (CAN), it is serial data communications network used within vehicles, we can have access to it by the OBD-II module, which is an onboard diagnostics, this is from the 80-90s so the protocol is not as good as it could. In the CAN bus there is no authentication way so any message in the CAN Bus is trusted. There is only three ways of getting to the CAN Bus:
- Attack the exploit to OBD-II, this requires physical access to the car.
- Exploit over the onboard cellular, most cars have separate networks for this, but what if they don't.
- Exploit over onboard Wi-Fi.
19.4 IoT Vulnerabilities
Most of these devices they use Linux or Android as their OS, so the vulnerabilities from these OS apply to them. They must be updated always as soon as possible. Most IoT are not secure; so we need to segment them to their own network if we really need to use them.
19.5 Embedded System Vulnerabilities
A specific system design to perform a specific dedicated function, they can be very simple or very complex; these systems almost never received updates and they are secure because they have very little code but also they have very little security. The Programmable Logic Controller (PLC) is the computer used to monitor and automate mechanical systems, with these we receive very little updates, we also have System-on-Chip (SoC) that are used along with embedded systems.
19.6 ICS and SCADA Vulnerabilities
Operational Technology we use control system to control systems, not endusers but controls for vaults in a building or similar, here we must prioritize availability and integrity over confidentiality. Industrial Control System (ICS) is the system used to control all the devices used, for example to control the devices in an electrical power station or a hospital, they use Fieldbus to link devices and communicate with each-other; a Human-Machine Interface (HMI) is something that allows the users to control these things; a Data Historian is a system that allow us to collect data of what has happen. Supervisory Control and Data Acquisition (SCADA) is the control system that manages large-scale systems, the difference is that ICS manages one organization or building, but SCADA can manage multiple of them, this is like a central server. Modbus gives control server and SCADA hosts the ability to query and change the systems.
19.7 Mitigating Vulnerabilities
The go-to page is the NIST page; but we can do four key controls:
- Establish administrative control over Operational Technology (very different to IT) networks.
- Implement the minimum network links by disabling unnecessary links, services and protocols.
- Develop and test a patch management program for the OT networks.
- Perform regular audits and logical physical access to the systems to detect vulnerabilities.
19.8 Premise System Vulnerabilities
These are systems to build automation and physical access security, for example the RFID keys, or the security systems; they usually allow to be monitored over the network but can make them hackable. Building Automation System (BAS) are components and protocols to centralize the configuration and monitoring of the devices in the building network, like backup batteries for the building, like the things that control elevators in movies; these should be in their own system network but then we have the process and memory vulnerabilities in PLC, and the problem is that these systems may have plaintext credential, and they are also vulnerable by code injection via the web interface; these are critical since we could be victims of a real Denial of Service. The Physical Access Control System (PACS) is the components and protocols that facilitate the configuration and monitoring of security mechanisms within offices and data centers, the problem is that they are usually maintained by external providers so they can be overlook by our test but we need to take them into consideration and request security reports so we don't trust them.
20. Authentication
The usage of Multi-Factor authentication is highly recommended, five types:
- Knowledge.
- Ownership.
- Characteristic.
- Location.
- Action. A HMAC-based is a One-Time Password shared synchronized between the client and the server.
20.1 Authentication Models
There are:
- Context-aware Authentication: usually restricts the time, day or location from were the user can access from.
- Single Sing-On (SSO): establishes an user profile and link all the resources needed so the user only need one long strong password; the problem is that one SSO compromised password is very dangerous.
- Federated Identity Management (FIdM): a single user identity created and shared for multiple organization but following an standard.
- Security Assertion Markup Language (SAML): an attestation model built using XML.
- OpenID: for example Google Sign-In; it is easier to implement than SAML.
20.2 802.1x
Standard framework used for port-based authentication ; either wired or wireless.
20.3 LDAP and Kerberos
Is a database used to centralized information , uses port 389 when unencrypted and 639 when encrypted; the Microsoft Implementation is Active Directory. Kerberos is an authentication protocol for multiple authentication steps.
20.4 Remote Desktop Service (RDP)
It was develop by Microsoft, allows users to control the computer as if they are in front of it, however does not provide strong authentication; the alternative is Virtual Network Computing (VNC), should be used when something beyond Windows domain, this uses port 5900 (should be tunnel via SSH) and RDP uses 3389.
20.5 Remote Access Service
PAP is an authentication protocol, but it is very old and very unsecured and should not be used. After this came Challenge Handshake Authentication Protocol, the server encrypts a random string, sends them and the user makes a hash operations and send the results and the server checks if it is correct; if it is then it logged.
20.6 VPN
Builds a tunnel in an unsecured network, they are usually Client-to-Site VPN but they can also be Remote Access VPN and connect two offices. VPNs are very important, they keep our connection secure and encryption; they use two protocols different. A server is needed to make the VPN work, or we can have a VPN Concentrator. We should prevent split tunneling (accessing different the intranet and the internet) since this could be very unsecured.
20.7 RADIUS vs TACACS
RADIUS provides dial-up, VPN and wireless authentication, it is a client side and runs on the 7 layer of OSI; this is the AAA (Authentication, Authorization and Accounting); they run on port 1645-1646; TACACS is this but implemented by CISCO, runs on port 49 but it is cross-platform.
20.8 Authentication Attacks
- Spoofing: the goal is assuming the identity of someone else, usually tried by Man-in-the-Middle.
- Man-in-the-Browser: intercepts the API calls from browsers.
- Passwords Attacks: one of these is password spraying.
- Credential Stuffing: can be prevented by not reusing password.
- Broken Authentication: a software vulnerability where the attacker gets access, for example making very weak password requirements; or even like credential exposure or session hijacking.
21. Access Control
21.1 Models
- Discretionary Access Control (DAC): every file is consider an object, and the owner decides who can access that object. Every object must have an owner, each owner determines the access rights and permissions for each object, which means they have a lot of control.
- Mandatory Access Control (MAC): the computer decides who has access to what
objects, they do it by data labels for all subjects and objects. High, medium and low trust; so the
computer decides who can access something; compares the labels and if we have the minimum or above we
have access; but they also have the need-to-know; this can be implemented by Rule-Based or
Lattice-Based. This can be used in complex systems since this is very expensive to maintain.
- Rule-Bassed: compares the subject labels to meet rules.
- Lattice-Based: uses complex maths operations to know who can access.
- Roles-Based Access Control (RBAC): works by roles, and according to those roles the people can access some data; we set permissions based on the user's job. Power Users is a special user which has a little more permissions; we can do a lot of things with this.
- Attribute-Bassed Access Control (ABAC): uses conditionals to determine if we can access something or not for example if I am from CyberOps I can access some tools; this is very dynamic.
21.2 Best Practices
- Implicit Deny: all access to resources should be denied until I need to give access to someone, unfortunately the systems are built otherwise.
- Least Privilege: users should only have the lowest level of access needed to perform their job.
- Separation of Duties: for example some task we need two of more things to sign off for it to prevent data loss or similar.
- Job Rotation: this allows us to detect some suspicious made, like fraud.
21.3 Users and Groups
We can have multiple users and groups, these makes groups deeper and deeper. We can limits almost
anything we want using Active Directory and we should always trust no one when configuring. Permissions
can usually be read, write and execute but in Windows there are a few more. In Linux we set this by
using chdmod this is Read(4), Write(2), Execute (1); if we have multiple of these we sum,
and from here we assign by Owner, Groups, AllUsers; like 777 means that everyone has all permissions.
Privilege Creep is when by accident we have additional permissions through different roles, this should
not happen; to solve this we use User Access Recertification, so every user's permissions are
checked time to time, like for example every year; any hiring, firing or promotion should trigger this
review.
21.4 Permissions
Inherited happens automatically when a new group is created under a new group, so this new has all the permissions from the parent. From the parent to a child is called propagation; sometimes we want this to happen and sometimes we don't; we can disable inheritance from the properties. Groups should be assigned by roles and users always to roles, never set them individually; when we copy something it inheritance it to from the new folder; but if we move it it keeps the permissions set.
21.5 Usernames and Passwords
We need to always use strong passwords because the usernames can usually be easily guess; we should:
- Always required the user to change the password.
- The user needs to change the password every 90 days.
- Always change the defaults admin or root password, and disable that account.
- Disable the Guest account (Windows).
- Enable CTRL+ALT+DEL to log in, this prevents malwares from running automated.
- Use good, strong policies in regards to the passwords.
21.6 User Account Control
This UAC is a security component from Windows that allows us to always run as an standard user and only use admin privileges when strictly needed; this reduce the risk of malware; we can disable this but it is not recommended.
22. Risk Assessments
It is the probability that a threat will be realized, our job is to minimize vulnerabilities; we can not control threats but we can minimize them however. Risk is the interception between threats and a vulnerability. If we have identified possible threats then we can work on some possible solutions to minimize a negative outcome if something bad happens; with risk we can:
- Avoid it.
- Transfer it: for example if we have the risk of a hurricane we can buy an insurance.
- Mitigate it.
- Accept it.
- Residual: the risk remaining after trying all before, it is almost impossible that this does not exist; every organization have their own risk acceptance rate.
To make this we have to:
- Identify our assets.
- Identify our vulnerabilities.
- Identify the threats.
- Identify the impact if one of them is materialized.
22.1 Qualitative Risk
Uses intuition, experience and others to evaluate risk; for example us evaluating a course, in order to do this the people evaluating must have experience and knowledge. We do not need to do a complex algorithm to evaluate it.
22.2 Quantitative Risk
Uses numerical and monetary values to estimate the risk; we also estimate the magnitude of the impact resulting in a financial number, this allow organization to estimate the importance of this; it uses the:
- Single Loss Expectancy (SLE): cost associated with the realization of each individualized threat.
- Annualized Rate of Occurrence (ARO): how many times a year can happen.
- Annualized Loss Expectancy (ALE).
We use the ALE to take actions and create policies in the company. It is really important because otherwise we could spend much more money than needed. There is also a hybrid approach, IT directors are usually people with a lot of experience in order to use both models correctly.
The single loss expectancy (SLE) is the amount that would be lost in a single occurrence (AV) times the risk factor (RF). The annual loss expectancy (ALE) is the total cost of a risk to an organization on an annual basis. This is determined by multiplying the SLE by the annual rate of occurrence (ARO).
22.3 Methodologies
Security assessments are all type of test that allow us to test every security part of the organization; for example we can do an analysis from the inside but also from the outside of the organization. These type of assessments can also be required by some contracts and some type of organizations; these type can be active or passive.
22.4 Security Controls
There are three types:
- Physical controls.
- Technical controls: password, encryptions and etc.
- Administrative controls: changing the behavior of people instead of making something else, for example telling the people they must lock the computer every time they leave the computer, or such as mandatory vacations.
NIST also has other three:
- Managements controls.
- Operational controls: things done by people.
- Technical controls: logical controls put in a systems to help secure it.
Another one is:
- Preventative: controls for before something happen, for example a backup battery.
- Detective: used to find out whether something happened or not, for example CCTV.
- Corrective: for after something occurs, for example recovering data fast.
- Deterrent: may not physically or logically prevent access, but it serves to discourage an attacker from attempting an intrusion.
A single control can be categorized in multiple different categories, there is also a compensating control, which is something unusual, like an alternative that has a similar level of security.
22.5 Types of Risk
- External Risk: it is produced by non-human source, for example wild fires or natural disasters.
- Internal Risk: there are usual easy to see and therefore we may prevent them, for example that a server will die eventually.
- Legacy Systems: anything old or computer that is still in use, for example something using Windows XP.
- Multiparty: multiple systems or organizations connected and each of them brings their own inheritance risk.
- Intellectual Property Theft: someone may wants to still our information, like stealing a patent.
- Software Compliance and Licensing: for example if I still an external software, I am bringing the risk of that software to the organization.
23. Vulnerability Management
Seeks to identify any issues in a network, applications, database or any system prior to something bad happening. Once identified we may deploy countermeasures to prevent them; the process is scan, patch, scan and so on. We need to think of:
- Value: What is the value of what we could found; how important and private is something.
- Threats: what vulnerabilities is my system vulnerable to.
- Mitigations: what can we deploy to solve the vulnerabilities we found.
These are important since they allow us to focus where we need to solve things, these programs are conducted using some type of software for scanning or some type of pen-testing; these programs will categorize them and give them to us to take action; steps to conduct them are:
- Decide the desired state of security.
- Create a baseline, understand what is normal.
- Prioritize the vulnerabilities.
- Mitigate vulnerabilities.
- Monitor the network and systems, as well as performing future tests; this process will repeat.
23.1 Penetration Testing
Breaks into the systems just like a hacker, in a blackbox test however some organizations can hire pentesters as blackbox test. After the test we get a report of what they found; usual tools are Metasploit or CANVAS, this is something that has to be done time to time. They follow the steps:
- Get permissions & document info.
- Reconnaissance.
- Enumerate targets.
- Exploit the targets.
- Document the results.
23.2 OVAL
It is standard design to regulate the transfer of secure public information, make of a language (XML scheme) and an interpreter.
23.3 Vulnerability Assessments
Tools used to conduct these:
- Network Mapping: discover and document of physical and logical connections in our network; Solarwind, Zenmap are graphical tools that can map our network.
- Vulnerability Scanning: identifies threats but they do not exploit them, some may just find open ports and other more advanced can go deeper.
- Banner Grabbing: get info from the system and inventor their systems; some tools are Nessus or Qualysguard.
- Network Sniffing: analyzing the traffic or capturing the packets going in the network of anyone.
- Protocol Analyzer: taking these packets and reconstruct them almost identical, like Wireshark.
Password Analysis It is a tool used to test the strength of our password, they are also crackers; the most common are Cain & Abel, and John the Ripper. We can do several attacks:
- Password guessing: we just got lucky trying to guess someone's password having some key info.
- Dictionary Attacks: having a list of possible passwords, some hackers may have their own personalized dictionaries.
- Brute-Force Attack: trying every possible combination, amazingly slows but sure, complex strong password are a must nowadays.
- Cryptanalysis Attack: computing a precomputed encrypted password to a value in a lookup table this is call a rainbow table, and just compare the encrypted value and then check their unencrypted value. Crackstation is one of the best rainbow tables.
- Rubber Hose Attack: someone forcing other to tell their password, using violence.
24. Monitoring & Auditing
Monitoring is trying to find whatever is not good, either by signature-based (detecting predefined patterns), or anomaly-based (establish what is normal and then set to analyze everything else), or behavior-based (an activity analyzed based on previous set things but this sets a lot of false positives); however we can use multiple of these (a hybrid approach).
24.1 Performance Baselining
It is the process of measuring changes in a network, hardware and software; this helps us define what is normal. A security posture is the risk level to which a system is exposed. We can monitor operations and functionality, how much something is used, so we can detect something anomalous; we can make reports to compare it, in Windows we can use Perfmon.exe.
24.2 Protocol Analyzers
It is use to capture and analyze network traffic. They can be in promiscuous mode (captures all the traffic regardless of MAC address); otherwise we will only capture the traffic coming to us.
24.3 Simple Network Management Protocol (SNMP)
This is incorporated in network management, has three components:
- Devices.
- Agents.
- Network Management Systems (NMS). In security there are three versions, v1 and v2 are insecure, we should only use v3, provides encryption messages.
24.4 Auditing
It is a detective control, we look to see if everything is under control, we can review logs, ALC, user rights and permissions, vulnerability scans and else; logs are usually very important for this since they tell us what is right and what is not.
24.5 Logging
Data files containing accounting and audit trails, they tell us what has been done in the endpoint; in Windows there are security, system and applications logs:
- Security Logs: successful and unsuccessful logins to the systems.
- System Logs: such as driver failures and shutdown.
- Application Logs: third-party applications. To view these in Windows we can use the EventViewer, but we can use SYSLOG to do it more efficient, this uses port 514 over UDP.
24.6 Log Files
They allow us to reconstruct an event after it occurred. We need to configure these files properly, do we want to log everything, how often do we want to take them out and else; they should be save on an external server or device so if the server is damaged we can take them from somewhere else. We need to think in every possible event in the case that the logs are very big or that we run out of space or if we get to the maximum capacity; these files should be archived and backed up using Write Once Read Many (WORM), if someone hacks they can not delete them, and how can we even protect these files internally like encrypt them keeping them out of people eyes.
24.7 Security Information and Event Management Systems (SIEM)
Logs should not be review inly after an incident, they should be review constantly. We need to establish and document the scope of event, as well as develop use cases to define a threat, and plan incident response plans before an event, we need to establish a ticketing process to track events, also schedule threat hunting and finally provide auditors and analyst an evidence trail. There are many SIEM solutions:
- Splunk, can be installed locally or cloud-based solution.
- ELK/Elastic Stack, it is a collection of free and open source tools for SIEMs.
- ArcSight.
- QRadar.
- Alien Vault and Open-Source Security Information Management (OSSIM), this can integrate other administrative tools to manage the whole security environment.
- Graylog, it is really focus on DevOps.
24.8 Syslog
A protocol to enable different apps to send logs, works with a client-server model. It usually runs on port 514 using UDP over TCP/IP. Using this protocol may generate issues so we need to solve this. Some solutions are call syslog-nexgen; syslog can refer to the protocol, the server or the log entries themselves.
24.9 Security Orchestration Automation and Response (SOAR)
It is a security tool that facilitates the incident response process, it takes a security information and monitoring systems and it is integrated with this SOAR. We can program playbooks, scan security and threat data, analyze the data with ML and automate data enrichment, and do incident response. A playbook is a checklist of actions to perform, detect and respond to a specific type of incident. A run-book is a lot of automations combined.
25 Cryptography
It is the practice of writing and solving codes to hide the true meaning of something, usually refer as encryption, we use it for data at rest, in transit and in use. The important part is the key. A cipher is an algorithm that performs the decryption or encryption; these are mathematical functions. If we are able to make the algorithm public then we have a good algorithm because the key is the secure part.
25.1 Symmetric vs Asymmetric
These are categorized for the cipher, symmetric we have only one key to both encrypt and decrypt (these are usually call private key); asymmetric is when we have one key for encryption and one for decryption (this is call public key); with private key we can not have non-repudiation policy, also the key distribution is a problem. Using asymmetric algorithms we have a public key, non of them are better since they are for different purposes. Most things uses hybrid implementations; public key is slower so usually people sends the symmetric key transfer over asymmetric. Block Cipher os break the message into fixed-length blocks of data and performs the encryptions, encrypts by blocks. Stream cipher are the contrary and are usually used in hardware.
25.2 Symmetric Algorithms
Some of the algorithms:
- DES: breaks the input into 64-bit key, now it is not usually used since can be easily breakable.
- 3DES: there were 3 64-bit keys used, it jumped into the function three types, however it was slow.
- IDEA: uses a 64-bit key.
- AES: replacement for DES, using 128, 192 or 256 bit key. It is the standard encryption for US.
- Blowfish & Twofish: supposed to be the AES but was not taken.
- RC4, RC5, RC6: can be used 40-2048 bits encryption; this is used in the SSL. Only RC4 is stream cipher, all the other are block cipher.
25.3 Public Key Cryptography
This covers the confidentiality, integrity, authentication and non-repudiation. We encrypt something using the public key and decrypting it using the private key; and from the other part anyone can see by my public key that I was the one that sent a message but this is how it should be. A digital signature is a hash used to let the recipient know who sent the message. Asymmetric encryption is know as public key and uses to two keys, one for encryption and one for decryption.
25.4 Asymmetric Algorithms
They are:
- Diffie-Hellman (DH): it is used for key distribution, this means sending a private key, however it is vulnerable to Man-In-The-Middle attacks. It is usually used for VPN configurations.
- RSA: digital signatures, uses private key pairs between 1024-4096 bits algorithms.
- Elliptic Curve Cryptography (ECC): it is very efficient, it is very used in mobile devices since they do not have a lot of computer power. There are some variants combining this with DH for example.
25.5 Pretty Good Privacy
This is the program (PGP) used to encrypt emails but not is used to encrypt files, it uses IDEA but as a hybrid cipher implementation. Uses 128 symmetric functions or 512-2046 for asymmetric functions.
25.6 Key Management
Refers to how an organization generates, exchanges and stores the encryption keys; the encryption relies in the key strength, not in the algorithm. Keys must be securely stored and periodically change.
25.7 One-Time Pad
It is a stream cipher that encrypts with the same length as the plaintext input. Once that the code is used it is destroyed, not mathematic function was used. There is one problem that is that no computer can create truly random numbers so another computer may reverse engineer this.
25.8 Cryptography Considerations
- Blockchain: a shared, immutable ledger to commute transactions; mostly used for cryptocurrencies.
- Public Ledger: a system that keeps participants identities secure and anonymous, it is decentralized so no one can change it without authorization.
- Quantum Computing: we used superposition bits, this is a very big problem for encryption.
- Post-quantum Cryptography: it is something done with today's computer but that can not be break with quantum computing.
- Ephemeral: a cryptographic keys used to be short-lived and used to exchange key, for example it is used in WPA3.
- Homomorphic Encryption: allows calculations to be performed on data without decrypting it, can be used for privacy-preserving outsourced storage and computation, this is perfect for example for cloud computing so the vendors can perform the operations they need without watching our data if this type of encryption is supported.
26. Hashing
It is a one-way cryptographic function that takes an input and makes a unique message, makes it a digital print, and the output is always the same length, the most common one is MD5, when two files has the same hash it is call a collision, SHA is the replacement for MD5. SHA-3 is the newest, has the 224 and 512 bits. Hashes are used to assure integrity (like digital signatures); the most commons are MD5 and SHA-Families.
26.1 REPIMD & HMAC
They are open-source hashing algorithms. To prevent a collision to happen we can use a digital signature, which is a to create the hash and then encrypt it for sending, this will also makes a non-repudiation solution, this makes that we can assure the other was the one sending the message. DSA and RSA are some algorithms for digital signatures.
26.2 Code Signing
It is a key used to assure that the software has not been modify since the developer published.
26.3 Passwords
No passwords in Windows are saved in plain text, they are saved in hashes. LANMAN (LM Hash) is the original version of hashes but it is very weak and should not be used. On modern Windows systems is NTLMv2 hash the one used to hash the passwords when saving.
26.4 Hashing Attacks
- Pass the Hash: hacking technique to authenticate using the hash stored, they do not need to brute-force the password, they only need the password; it is very difficult to defend from it. many tools can do this, like Mimikatz; to prevent this we need to make sure updates are done and least privilege.
- Birthday Attack: when attackers makes an intentionally collision, to attack a system matching the password hash even by entering the wrong password.
26.5 Key Stretching
It is a function to pass weak hashes and make them stronger without changing then to make them more difficult to crack.
27. Public Key Infrastructure
Also know as PKI, uses asymmetric encryption. Works when we connect to a website, we go to a public key infrastructure and we request the public key which we will use to encrypt and then no one can see what is traveling because it is decrypted using the private key. PKI is a system that creates pairs of keys to make a sure and safe connection, but we also need the Digital Certificate.
27.1 Digital Certificates
It is a digitally signed document that binds a public key to an user. The X.509 is the certificate that can be used for multiple domains, a wildcard can be used but if this one is vulnerable then all the domains will lose the certificate. The SAN (Subject Alternative Name) is what allows a user to assign domain and IP Address to this domain. Some certificates do dual-sided certificates which is make the server and user to validate the certificate but this makes double the work.
- PEM is used for electronic mail.
- P12 is used to store a server certificate and a private key together.
- PFX is the personal information exchange, stores the public and private key.
- P7B is used for Single-SigOn.
27.2 Certificate Authorities
They are the ones that creates the certificate, they are many of these authorities, to validate the authenticity, they also keep a copy. They also have a certificate revocation list, a list of compromised certificate that has ever been revoked, they always checked when we make connection. Trusting a parent is called Transitive Trust.
27.3 Online Certificate Status Protocol (OCSP)
This protocol is like an open-source of this to be faster but less secure.
27.4 Public Key Pinning
Makes the header strong to avoid impersonation of certificates.
27.5 Key Escrow & Key Recovery Agent
It is a secure copy of a user’s private key in case accidental key lose. It is a software that allows restoration of the keys. If one certificate is make vulnerable then all certificates created by that authority must be revoked and new ones made.
27.6 Web of Trust
It is decentralized model that addresses the issues of having to pay these things, but we made a peer-to-peer trust. We can have a self-signed certificate, we can choose to trust the website of not, it is not a good idea to trust the certificates. We can also trust the public intelligence, to know if we should trust a website or server.
28. Security Protocols
28.1 S/MIME
It is the standard that provides cryptographic security for emails, uses separates keys for every email sent and received. The problem is that encrypts all contents, even malware, which makes the filters and other things vulnerable; so some emails providers will load the private key to decode previous to received it.
28.2 SSL/TLS
It is used for web security. These protocols can be used with other protocols, for example TLS is mostly used with HTTP. Or we can also used it with emails to ensure encryption. TLS can be attack by a downgrade attack, which is tricking the protocol to use an older version of TLS that is vulnerable so can be exploit, web servers can be configured to never downgrade. Break and Inspect is acting in the middle to see what is coming and make sure that no malware is coming in.
28.3 SSH
It is a protocol to create a secure tunnel in which I can control another system remotely, it was created to be a replacement to TELNET and it has become very popular. We need a server (daemon) and the a device that runs as a client, it usually works in port 22. The new versions added MACs and Diffie-Hellman keys exchange.
28.4 VPN Protocols
- PPTP: Point To Point Protocol encapsulates the packets, works in port 1723, and uses CHAP-based authentication and should have strong authentication since can be vulnerable.
- L2TP: Layer 2 Tunneling Protocol: it is not secure because it is usually paired with IPSec to work together since this one runs in private networks. IPSec: authenticates and encrypts IP packets, it provides confidentiality, integrity and authentication and can be set in Main, Aggressive or Quick mode. A Security Association (SA) it is an establishment of secure connections that shares certificates. IPSec can work in Transport Mode (does not include the header encryption) people know where came from but not what; in the Tunnel Mode both header and content are encrypted, it is used to transmit information over unsecured networks.
29. Planning for the Worst
Redundancy is something extra or unnecessary, however in IT this is super important in case something fails. A Single Point of Fail is a point that if fails all the system would fail. Mission essential functions are things that must be performed by an organization to meet its mission.
29.1 Redundant Power
It is an enclosure that provides power supplies to make sure that power always exist. A surge is an unexpected increase in the amount of voltage if it is big it is called a spike, to protect agains this we should use as surge-protector. A sarge is when the voltage decreases, a Brownout is when it decreases so much that the computers fail. A blackout is a total loss of power for long time.
29.2 Backup Power
An UPS is a battery to keep the computer working, however they can only last at most one hour. generators are:
- Portable Gas: uses gasoline or solar power and they are usually very loud.
- Permanently Gas: more complex to install but they are always there, they use natural gas.
- Battery Inverted: requires very little interaction they can be combine with others.
29.3 Data Redundancy
All these is done by software; using a RAID we need to know the types:
- RAID 0: provides data striping for multiple disk.
- RAID 1: uses two identical disk.
- RAID 5: requires at least 3 disks to work, it has very good redundancy.
- RAID 6: modified form of a RAID 5, it has two stripes for parity data, we need at least 4 disk.
- RAID 10: combines the RAID 1 and 0; gives a redundant mirror and it is fully redundant.
- Disaster-Tolerant RAID.
29.4 Network Redundancy
We should have multiple switch and routers in order to have backups.
29.5 Server Redundancy
To achieve this we need to do clustering, which is making two servers work together to make a particular job. We can configure then for failover or load-balancing cluster for example when we need high computing power or for example a busy website server.
29.5 Redundant Sites
We need to have a redundant place to work in case our building has a catastrophes; a hot-site is ready within minutes, a warn-site has computers and servers but not everything is updated; and a cold-site will only have the basic phones and services and nothing is configure it will take a few days to have ready; this will depend on the company needs.
29.6 Data Backup
- Full Backup: all contents of the drive are backed up.
- Differential: only conducts a backup of what have changed since the full backup.
- Incremental: it is similar to differential, but differential makes quick backups but incremental makes the copy faster.
29.7 Tape Rotation
- 10 Tape Rotation: a simple method that provides access to the entire set.
- Grandfather-Father-Son: sets of backups.
- Towers of Hanoi: same sets of backups but they are rotated different, it prevent then from fails but it is more complex.
- Snapshots: they are very good but take a lot of space.
29.8 Disaster Recovery Plan
A plan in case anything happens, can be natural disasters or fires or even cyberattacks. A good plan must be written down and a lot of people should have an idea of what to do; and we also need to have the contact information, calculate the impact determination and the recovery plan which is knowing what to do; and have copies of agreements, and do disaster recovery exercises for the employees to know what to do, at least once a year; and we need to have a list of critical systems and data to know what recover first.
29.9 Business Impact Analysis (BIA)
We need to measure our business in metrics that give us an idea of how are we working in case of disasters. Based on all these metrics we will need to make the plans and countermeasures.
- Maximum Tolerable Downtime (MTD): how long can we be down without going out of business, this sets the upper limit that the plan will have.
- Recovery Time Objective (RTO).
- Work Recovery Time (WRT): we may have the main problem but how long do we take to have the works back.
- Recovery Point Objective (RPO): how long can we be without our data without catastrophic consequences.
- Time Between Failures: consider possible fails while solving a previous problem.
- MTTR: represents the time to repair some component or device.
- MTBF: represents the mean time between inherent failures of a system during operation.
30. Social Engineering
Anything that manipulates users into revealing secret information. Sometimes if we use major or common names, it is possible that even if we are incorrect they can correct us and give us info.
30.1 Insider Threat
Employees that give access to external people, they may be motivated by money and sometimes we do not monitor for insider threats; we need to have Data Loss Prevention (DLP) systems.
30.2 Phishing
Spear phishing is personalized phishing attacks to a specific user. Whaling is spear phishing but for major executives in the company (like the CEO, CISO). Smishing is by using text messages. Vishing is phishing through a phone call. Pharming is tricking an user to go to a fake website.
30.3 Motivation Factors for Falling
- Authority: people can obey more if the order is coming from an authority like a boss.
- Urgency: pretend to have a deadline.
- Social Proof: people are more likely to click on something that is popular or have comments.
- Scarcity: something like urgency but it is usually through emails, like "click here, iPhone free".
- Likeability: friendly and cute people get doors opens that most people wouldn't.
- Fear: it is widely used in ransomware.
30.4 More Social Engineer
- Diversion Theft: that something out of way to steal it.
- Hoax: attempting to deceive people in believing something false.
- Shoulder Surfing: getting credentials by watching someone type.
- Eavesdropping: overhear some private information.
- Dumpster Diving: when someone goes to garbage trying to find important information.
- Baiting: when a person leaves a malicious USB in some place hoping someone pick it and plugged in their computer to install malware.
- Piggybacking: when someone takes an unauthorized person to a restrictive area.
- Watering Hole Attack: they figure where we like to go and they put the malware there and trick us to download it.
30.5 Fraud and Scams
Fraud is tricking someone to give us something, the most common is identify fraud (steal someone's identity). Identity fraud is just to make transactions like if I was you. Scam is a fraudulent act or operation; the most common is an invoice scam, tricking someone to pay for something they did not order, happens a lot with office supplies. These techniques are not very technical but they can be as well like prepending by tricking users to give their credentials, can be done by using large URLs.
30.6 Influence Campaigns
It is very used for military purpose since they know how important is this; for example if Russia wants to influence a country to vote for some candidate specifically. This is a form of hybrid warfare.
30.7 User Education
We can have all the measures that we want but if the users are vulnerable then everything else will not work.
- Never share authentication information, nor id badges.
- Clean Desk Policy.
- Train them on how to protect the email, using encryption.
- Never pick up nor use any removable media.
- Physical paper is destroyed first.
- Make sure they follow the company policies for dispose things.
31. Policies and Procedures
All these is used to determined the level of security of which the organization should have. They can be:
- Organizational.
- System-Specific.
- Issue-Specific.
They can be further separated in:
- Regulatory.
- Advisory.
- Informative.
A baseline is the reference in which all other servers or services will be compared as an idea of the goal. Guidelines tends to be a bit flexible, they recommend some actions. Procedures are step by step instructions created by a given action, for example on how to create a new user account. Most of these things are already created but we can create our own. The most important is that policies are generic guidance, procedures are specific.
31.1 Data Classifications
Sensitive data is any information that can create a loss of security of advantage to a company, but they have classifications, and a problem is over classifying data; if the company is commercial then classifications are:
- Public Data: will have no impact to the company if released.
- Sensitive Data: minimal impact on the company.
- Private Data: personal records, salary informations.
- Confidential Data: highest classifications and even source code.
Now if we are a government the classifications are:
- Unclassified: can be released to the public.
- Sensitive but unclassified: impact a few people but not a national security threat.
- Confidential: seriously affects the government if released.
- Secret: can damaged the government.
- Top Secret: gravely damage the government. The data should not be store forever because this will increase a lot of costs.
31.2 Data Ownership
- Data Owner: an executive role that has the responsibility of the asset.
- Data Steward: someone focused on working that the data is correctly labeled.
- Data Custodian: responsible of the management of the system in which the data is stored.
- Privacy Officer: responsible of the oversight of any asset managed by the company. The data owner should be someone from the business, the IT the custodian. Personal Identifiable Information (PII) and PHI If a piece of data can be used alone or in combination to identify someone then this is consider PII; also the PHI is consider the Personal Health Information. The Privacy Act of 1974 concerns anything related to personal data, the other is HIPAA, which is related to medical data, SOX is related to public-traded US companies, if this one is failed to follow the CEO can go to jail, the GLBA affects financial institutions, other one is FISMA, PCI DSS for credit cards, HAVA for security of the systems of election cycles, and the SB 1386 for data breaches in CA.
31.3 Legal Requirements
GDRP requires a data breach notification within 72 hours, breaches can always happen but there are many regulations that we have to comply, and the breach is not always a hacker but someone that made a mistake, GDRP gives stronger protection that in the US.
31.4 Privacy Technologies
Deidentification is the method of removing identifiable information from the documents before being released, we have to be careful of reidentification; can be:
- Data masking: replacing labels with generic data from the real data; covering the data.
- Tokenization: a unique token is substituted for the real data, we should be able to go back and retrieve the original data.
- Aggregation/Banding: gathering the data and generalize it to the protect the individual involved.
31.5 Security Policies
We have a separation of duties, can also be called dual control or split knowledge, we need at least to people to solve something. Job Rotation is when different users are trained to perform the task of some position, so we can change the person in charge and see if someone is doing something bad; we can do mandatory vacations too; also onboarding and offboarding when hiring/firing is important.
- Due Diligence: ensuring the IT risk are known and managed properly.
- Due Care: mitigation actions taken to defend agains risk discover during due diligence.
- Due Process: a legal term done for example to spy a phone.
31.6 User Education
- Security Awareness Training: reenforce the users importance to help secure the organization, this is the best return in investment of security policies.
- Security Training: teach users skills to help them do their job more securely.
- Security Education: generalized ideas of security, like this training. Specialized training is also necessary, or can even be for something specific.
31.7 Vendor Relationship
- NDA (Non-Disclosure Agreement): they are binding contract.
- MOU (Memorandum of Understanding): a formal/legal way of a formal agreement.
- SLA (Service-Level Agreement): the ability to support respond times to a problem.
- ISA (Interconnection Security Agreement): what each organization needs to meet.
- BPA (Business Partnership Agreement).
31.8 Disposal Policies
When a system is no longer needed. For example degaussing is destroying hard disks; purging os deleting data in a way that can not be restore; another way can be to encrypt the drive and delete the key; or clearing which is removing some part of the data in a way that can not be reconstructed. Data remnants is left small parts of data left in the disk.
31.9 IT Security Framework
- SABSA: risk-drive architecture, that think in any possible scenario.
- COBIT: divides IT in four domains.
- NIST SP 800-53, there is also the ISO 27000.
- ITIL: is the default standard for IT management, it is good to know for job interviews.
31.10 Key Frameworks
- Center for Internet Security (CIS).
- Risk Management Framework (RMF): integrates security in the development cycle, it was developed for the government and was created by NIST.
- Cybersecurity Framework (CSF): created by NIST but for organizations; consist of identify, protect, detect, responder and recover.
- ISO 27001: it is an international standard.
- ISO 27002: provides recommendations.
- ISO 27701: privacy extension to the 27001.
- System and Organization Controls (SOC): reports produces during an audit, makes sure that audit are followed.
- Cloud Security Alliance's Cloud Control Matrix.
- Cloud Security Alliance's Reference Architecture.
32. Incident Response and Forensics
The systems can never be 100% secure; an incident response is a procedure follow after a breach. A basic procedure is:
- Preparation: ensure to have a good plan and a good posture to limit the damage, before happen
- Identification: process of recognizing if something is a breach.
- Containment: isolating the incident.
- Eradication: remove the malware from the system.
- Recovery: re-enabling anything that was took offline before the incident, and add additional security so the problem do not happen again.
- Lessons Learned: identify what we need to fix for next time.
32.1 Incident Response Planning
Key people that respond to something set out by the plan. We must have:
- Manager: requires many soft skills and being public face to media and the executives.
- Analyst: determine what happened up to this point.
- Triage Analyst: work on the network during the response to monitor in real-time the incident.
- Forensic Analyst: find what has already happened and build a timeline.
- Threat Research: give intelligence during the response, and be up to date with latest threat.
- Cross Functional Support: people from many departments that help us with else, like lawyers.
This is known as a CSIRT and can be part of the SOC, this is a 24/7 job; we must have an updated contact list. We need to determined at what point we need to call the on-call person; we need to determined who to notified people, this depends on the organization procedures; how to contact them is also important and depends on the priority; and how far out we want this information to go.
The CSIRT will have to determine downtime, scope of the affected systems and else; we also need to see who are the affected stakeholders:
- Senior Leaders: executives and managers who respond for business operations, they have another coin face when we want to do something.
- Regulatory Bodies: for example the GDPR if something happened in European servers.
- Legal: they have to mitigate risk for civil lawsuits.
- Law Enforcements: this decision must be made with guidance from the Legal department.
- Human Resources (HR): used to ensure that are no breaches of employment law or contracts.
- Public Relations (PR): manage negative publicity.
32.2 Investigation Data
Security Information and Event Monitoring (SIEM), this help us given important dashboards, we need to think of the: sensors, sensitivity (how frequent we'll received info), trends, alerts and correlation. We also need to consider the logs, can be: network, system, application, security, web, dns, authentication, dump files (something that was dropped), VoIP and call managers; each of them should be correlated. Syslog/rsyslog/syslog-ng all these are the same, they take the logs and send them to a central point where we'll have them; journalctl, nxlog are platforms that help us analyze logs, this last one is cross-platform. netflow is used in networking created by Cisco and collect IP traffic; we also have sflow, it is an open-source or netflow.
Internet Protocol Information Export (IPfix) is used to facilitate how IP information should be formatted and transferred from an exported to a collector; basically a standard so the metrics are correct in every case. Metadata is very important too.
32.3 Forensic Procedures
Everything done is made done with compliance with the procedures, doing it always the same way:
- Identification: ensure the scene is safe and prevent evidence contamination, making sure is safe.
- Collection: we need to have authorization to collect the evidence and prove the integrity of the evidence as is collected, for example making an exact copy of the disk.
- Analysis: we make a copy of the evidence for analysis, everything is made by a procedure and made repeatable procedures.
- Reporting: create a report of the methods of what I found, how I found it, all locations, files, etc; everything we did is going to be tested for someone trying to make it invalid.
Legal Hold is a process designed to preserve all relevant information for a possible trial; we need to think in even having backup of the data in case the computer/server is taken away. We must have ethics:
- Analysis must be perform without bias, we do not judge on race, religion or else.
- Analysis methods must be repeatable by third parties.
- Evidence must not be changed or manipulated, we should never do analysis on the hard drive, instead to make a copy for analysis for modifying the things. Defense attorneys will try to use any deviation from these ethics as a reason to dismiss our findings and analysis. A timeline will show the sequence of file system events in a graphical form; it is very important to have some type of timeline, if it is not available automatically we may have to do it manually but should be included.
32.4 Data Collection Procedures
We use techniques to recover the system as quick as possible but also maintaining the evidence.
- Capture and hash the system images.
- Analyze data with tools.
- Capture screenshot, even of the machine.
- Review network traffic and logs.
- Capture video.
- Consider order of volatility.
- Take statements of witness and administrators.
- Review licensing and documentation.
- Track man-hours and expenses.
Data Acquisition is the method and tools used to create a forensically copy of data from a device, we need to know if we have the authorization to collect data, this could be an issue if the device is owned by the employee, we even need to consider that some data can be lost if the device is shutdown, this is the order:
- CPU registers and cache memory.
- RAM, routing tables, ARP Cache, temporary files.
- HDD/SDD/Flash Drive.
- Remote logging and monitored data.
- Physical configuration and network topology.
- Archival media. Important to know that the Windows registry is stored in some special part of the memory and so we should analyze the registry via a memory dump.
32.5 Security Tools
Networking:
- tracert/traceroute: display possible routes and measuring transit delays of packets across an internet protocol network.
- nslookup/dig: determined the IP Address associated with a domain.
- ipconfig/ifconfig: display currently connected network devices and can modify the configs.
- nmap: scanner of devices.
- ping/pathping: determine if a host is reachable on an internet protocol.
- hping: packet generator and analyzer for security auditing.
- netstat: displays the network connections for TCP, routing tables and a number or network instances.
- netcat: writing and reading using TCP or UDP so we can figure out information of a device, we can also have remote control but usually is blocked.
- arp: viewing and modifying the Address Resolution Protocol (ARP) cache on a given host or server.
- route: view and manipulate the IP routing table on a host or server.
- curl: used to transfer data to and from a server, can be used with many protocols, not only HTTP.
- the harvester: a python script to gather emails, domains, hosts, employee names and many more using key server and SHODAN database.
- sn1per: automatic scanner that can be used during a pentest to scan vulnerabilities.
- scanless: used to create an exploitation website that can perform open port scans, so we can hide
- dnsenum: used to enumerate DNS for server and organization.
- nessus: vulnerability scanner with remote capabilities, can scan servers and computers.
- cuckoo: automatic analysis for suspicious files.
File Manipulation:
- head: output the first 10 lines of a given file.
- tail: last 10 lines of a file.
- cat: output the full content of a file.
- grep: searching plain-text data using patterns or regular expressions.
- chmod: change the permissions of a file in Linux.
- logger: easy way to add messages to the /var/log/syslog file from the command line. Shell and Scripts
- SSH: encrypted tunnel.
- Powershell: task automation for Microsoft and the scripting language.
- Python.
- OpenSSL: a software library for applications that secure communications over networks.
Packet Captures:
- tcpdump: capture and analyze network traffic going through a system.
- tcpreplay: suite of free open source utilities for editing and replaying previous capture traffic.
- Wireshark: capture the packets and display them at a granular level.
Forensics:
- dd: command line used to copy disk images using a bit by bit process.
- FTK Imager: graphic tool used to determine if further analysis is required.
- memdump: cmd tool to dump a system memory that skips over holes in the memory map.
- WinHex: commercial disk editor used for data recovery and digital forensics.
- Autopsy: graphical user interface and digital forensics platform, make the cmd tools easy.
Exploitation:
- Metasploit Framework: tool that offer info on vulnerabilities, IDS signatures and improves pentests.
- Browser Exploitation Framework (BeEF): tool to hook multiple browsers to launch attacks.
- Cain and Abel: password recovery tool to sniff the network and do many things on passwords.
- Jack the Ripper: open-source password auditing and password recovery and cracking, like above.
